
Historically, most employees use Logitech wireless keyboards and mice. Once again entering our passwords, we, the Raccoon Security team, wondered: how difficult is it to bypass the security mechanisms of wireless keyboards? The study revealed architectural flaws and software errors that allow access to the input data. Under the cut - what we did.
Why Logitech?
In our opinion, Logitech input devices are among the highest quality and most convenient. Most of the devices we have are based on the Logitech Unifying solution - this is a universal dongle receiver that allows you to connect up to 6 devices. All Logitech Unifying compatible devices are labeled with the corresponding logo. An easy-to-use application allows you to control the connection of wireless keyboards to your computer. The process of connecting the keyboard to the Logitech dongle-receiver in detail, as well as the technology itself, is covered, for example, here .

Logitech Unifying Dongle Receiver
The keyboard can be a source of information for attackers. Logitech, taking into account a possible threat, took care of security - it used the AES128 encryption algorithm in the radio channel of the wireless keyboard. The first thought that an attacker can visit in this situation is to intercept key information when it is transmitted over the air during the linking process. After all, if you have a key, you can intercept keyboard radio signals and decrypt them. However, the user very rarely (or even never) has to associate the keyboard with a Unifying procedure, and a hacker with a scanning radio will have to wait a long time. In addition, not everything is so simple with the interception process itself. In a recent study in June 2019, security expert Marcus Mengs posted a message on the network about the discovery of vulnerabilities in older firmware for Logitech USB dongles. It allows attackers with physical access to devices to obtain radio channel encryption keys and to inject keystrokes (CVE-2019-13054).
We’ll talk about our Logitech SoC NRF24 dongle safety study from Nordic Semiconductor. And let's start with the radio channel itself.
How to "fly" data in the radio channel
For the time-frequency analysis of the radio signal, we used an SDR receiver based on the Blade-RF device in the spectrum analyzer mode (this can also be read about here ).

SDR Blade-RF Device
We also considered the possibility of recording quadratures of the radio signal at an intermediate frequency, and then analyzing them using digital signal processing methods.
The State Commission on Radio Frequencies in the Russian Federation allowed the use of short-range devices in the frequency range 2400–2483.5 MHz. This is a very “populated” range in which you can’t meet anything: Wi-Fi, Bluetooth, various remote controls, security systems, wireless detectors, mouse with keyboards and other wireless digital devices.
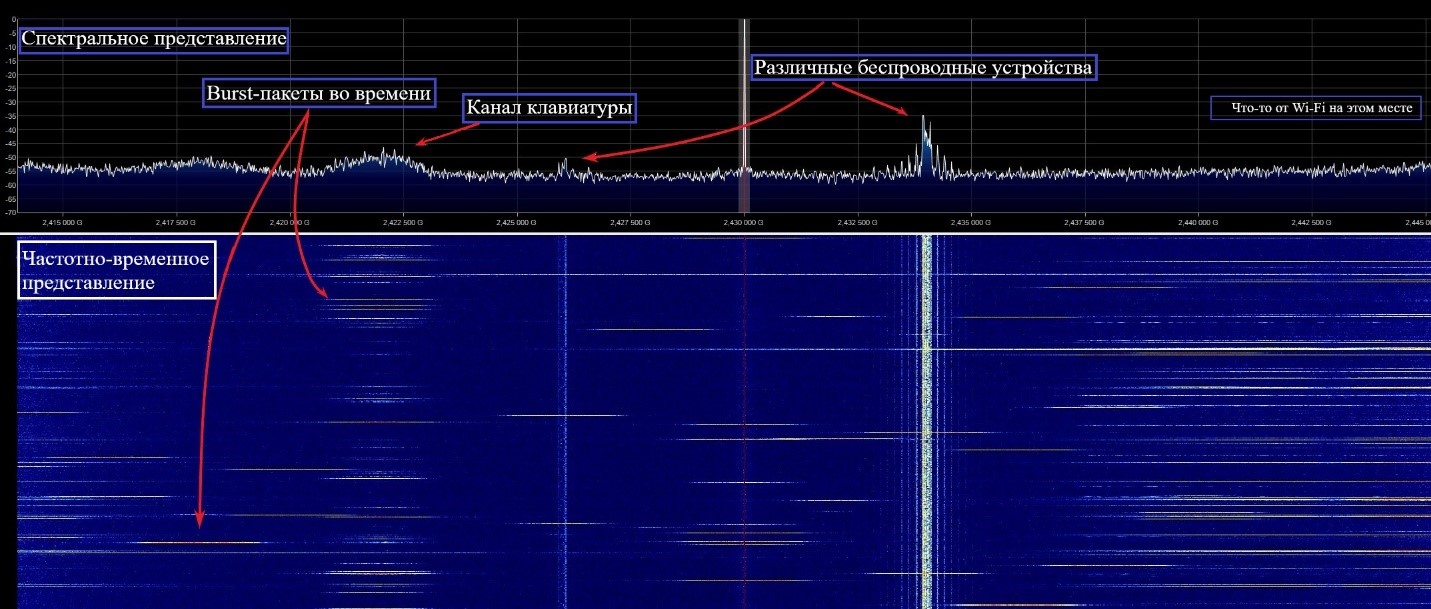
2.4 GHz Band Spectrum
The interference environment in the range is quite complicated. Despite this, Logitech was able to provide reliable and stable reception by using the Enhanced ShockBurst protocol in the NRF24 transceiver in combination with frequency adaptation algorithms.
The channels in the range are located at integer MHz positions, as defined in the NRF24 Nordic Semiconductor specification - a total of 84 channels in the frequency grid. The number of frequency channels simultaneously used by Logitech, of course, is less. We have identified the use of at least four. Due to the limited field of view of the signal spectrum analyzer used, it was not possible to determine the exact list of used frequency positions, but this was not necessary. Information from the keyboard to the dongle receiver is transmitted in Burst mode (by short switching on the transmitter) using the two-position frequency modulation GFSK at a symbol speed of 1 Mbaud:

Keyboard radio signal in temporary representation
The receiver uses the correlation principle of reception, so the preamble and the address part are present in the transmitted packet. No interference coding is applied; the data body is encrypted with the AES128 algorithm.
In general, the radio interface of the Logitech wireless keyboard can be characterized as completely asynchronous with statistical multiplexing and frequency adaptation. This means that the keyboard transmitter switches the channel to transmit each new packet. Neither the transmission time nor the frequency channel are known in advance to the receiver, and only their list is known. The receiver and the transmitter meet in the channel thanks to the agreed algorithms for bypassing and listening to frequencies, as well as Enhanced ShockBurst confirmation mechanisms. We did not investigate whether the channel list is static. Probably, its change is due to the frequency adaptation algorithm. Something close to the frequency hopping method (pseudo-random tuning of the operating frequency) is guessed in the use of the frequency resource of the range.
Thus, in the conditions of time-frequency uncertainty, to ensure the receipt of all keyboard signals, an attacker will need to constantly monitor the entire frequency grid of a range of 84 positions, which requires considerable time. Here it becomes clear why the vulnerability of key extraction via USB (CVE-2019-13054) in the sources is positioned as the ability to inject keystrokes, rather than gaining an attacker access to the data entered from the keyboard. Obviously, the radio interface of the wireless keyboard is quite complicated and provides reliable radio communication between Logitech devices in difficult interference conditions in the 2.4 GHz band.
A look at the problem from the inside
For research, we chose one of our Logitech K330 keyboards and Logitech Unifying dongle.

Logitech K330
Let's look inside the keyboard. An interesting element to study on the board is the SoR NRF24 chip from Nordic Semiconductor.
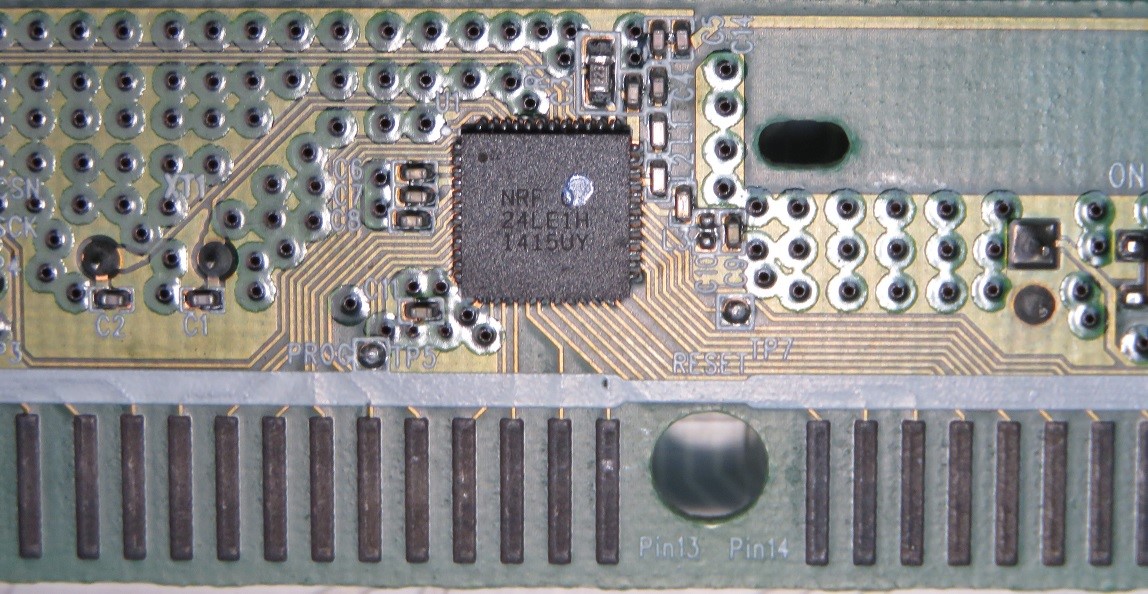
SoC NRF24 on Logitech K330 Wireless Keyboard
The firmware is located in the internal memory, the reading and debugging mechanisms are turned off. Unfortunately, the firmware has not been published in open sources. Therefore, we decided to approach the problem from the other side - to study the internal content of the Logitech dongle receiver.
The “inner world” of the dongle receiver is quite interesting. The dongle is easily disassembled, carries on board the familiar NRF24 in a release with a built-in USB controller and can be reprogrammed both from the USB side and directly by the programmer.
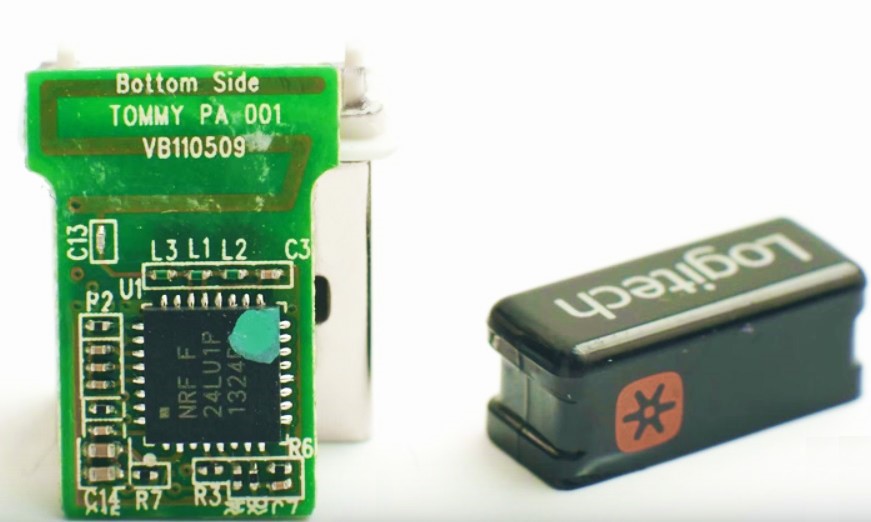
Logitech dongle without housing
Since there is a regular firmware update mechanism using the Firmware Update Tool application (from which you can extract the updated firmware version), there is no need to search for firmware inside the dongle.
What was done: firmware RQR_012_005_00028.bin was extracted from the body of the Firmware Update Tool application. To check its integrity, the dongle controller was connected by a loop to the ChipProg-48 programmer :

Logitech dongle cable to ChipProg 48 programmer
To control the integrity of the firmware, it was successfully placed in the controller memory and worked correctly, the keyboard and mouse were connected to the dongle through Logitech Unifying. It is possible to fill in the modified firmware using the standard update mechanism, since there are no cryptographic protection mechanisms for the firmware. For research purposes, we used a physical connection to the programmer, since debugging is much faster this way.
Researching firmware and attacking user input
The NRF24 chip is designed based on the Intel 8051 computing core in traditional Harvard architecture. For the core, the transceiver acts as a peripheral device and is located in the address space as a set of registers. The chip documentation and source code examples can be found on the Internet, so disassembling the firmware is not difficult. During reverse engineering, we localized the functions of receiving data on keystrokes from the radio channel and converting them to the HID format for transmission to the host via the USB interface. In free memory addresses, an injection code was placed, which included tools for intercepting control, saving and restoring the original execution context, as well as a functional code.
A packet for pressing or releasing a key received from a radio channel is decrypted, converted to a standard HID report and sent to the USB interface as from a regular keyboard. As part of the study, the most interesting part for us is the part of the HID report containing the byte of the modifier flags and an array of 6 bytes with keypress codes (for reference, information about the HID is here ).
HID Report Structure:
// Keyboard HID report structure. // See https://flylib.com/books/en/4.168.1.83/1/ (last access 2018 december) // "Reports and Report Descriptors", "Programming the Microsoft Windows Driver Model" typedef struct{ uint8_t Modifiers; uint8_t Reserved; uint8_t KeyCode[6]; }HidKbdReport_t;
Just before the HID structure is transferred to the host, the injected code takes control, copies 8 bytes of native HID data in memory, and sends it to the side radio channel in clear form. In code, it looks like this:
//~~~~~~~~~ Send data via radio ~~~~~~~~~~~~~~~~~~~~~~~~~> // Profiling have shown time execution ~1.88 mSec this block of code SaveRfState(); // save transceiver state RfInitForTransmition(TransmitRfAddress); // configure for special trnsmition hal_nrf_write_tx_payload_noack(pDataToSend,sizeof(HidKbdReport_t)); // Write payload to radio TX FIFO CE_PULSE(); // Toggle radio CE signal to start transmission RestoreRfState(); // restore original transceiver state //~~~~~~~~~ Send data via radio ~~~~~~~~~~~~~~~~~~~~~~~~~<
The side channel is organized at a frequency set by us with certain characteristics of the manipulation speed and packet structure.
The operation of the transceiver in the NRF24 chip is based on a state graph, into which the Enhanced ShockBurst protocol is organically entered. We found out that immediately before the HID data was transferred to the host USB interface, the transceiver was in IDLE state. This makes it possible to safely reconfigure to work in the side channel. The injected code intercepts the control, saves the original transceiver configuration in full, and transfers it to the new transmission mode on the side channel. The Enhanced ShockBurst acknowledgment mechanism is turned off in this mode, HID data in the clear is transmitted to the air. The structure of the packet in the side channel is shown in the figure below, the waveform diagrams were obtained after demodulation and before restoration of the clock data synchronization. The address value is selected for the convenience of visual identification of the packet.
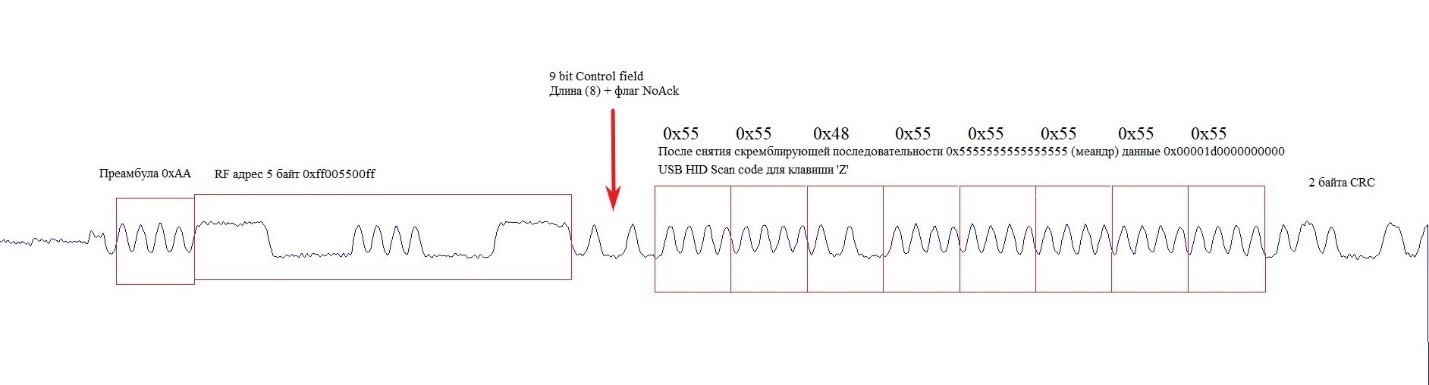
Burst Burst Demodulated Signal
After the transmission of the packet to the side channel is completed, the injected code restores the state of the transceiver. Now he is again ready to work in normal mode in the context of the original firmware.
In the frequency and time-frequency regions, the side channel looks as shown in the figure:
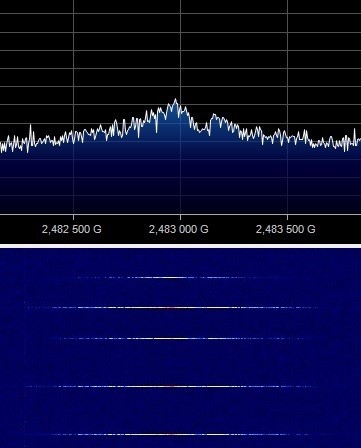
Spectral and time-frequency representation of the side channel
To test the operation of the NRF24 chip with modified firmware, we assembled a stand that included a Logitech dongle with modified firmware, a wireless keyboard and a receiver assembled on the basis of the Chinese module with the NRF24 chip.
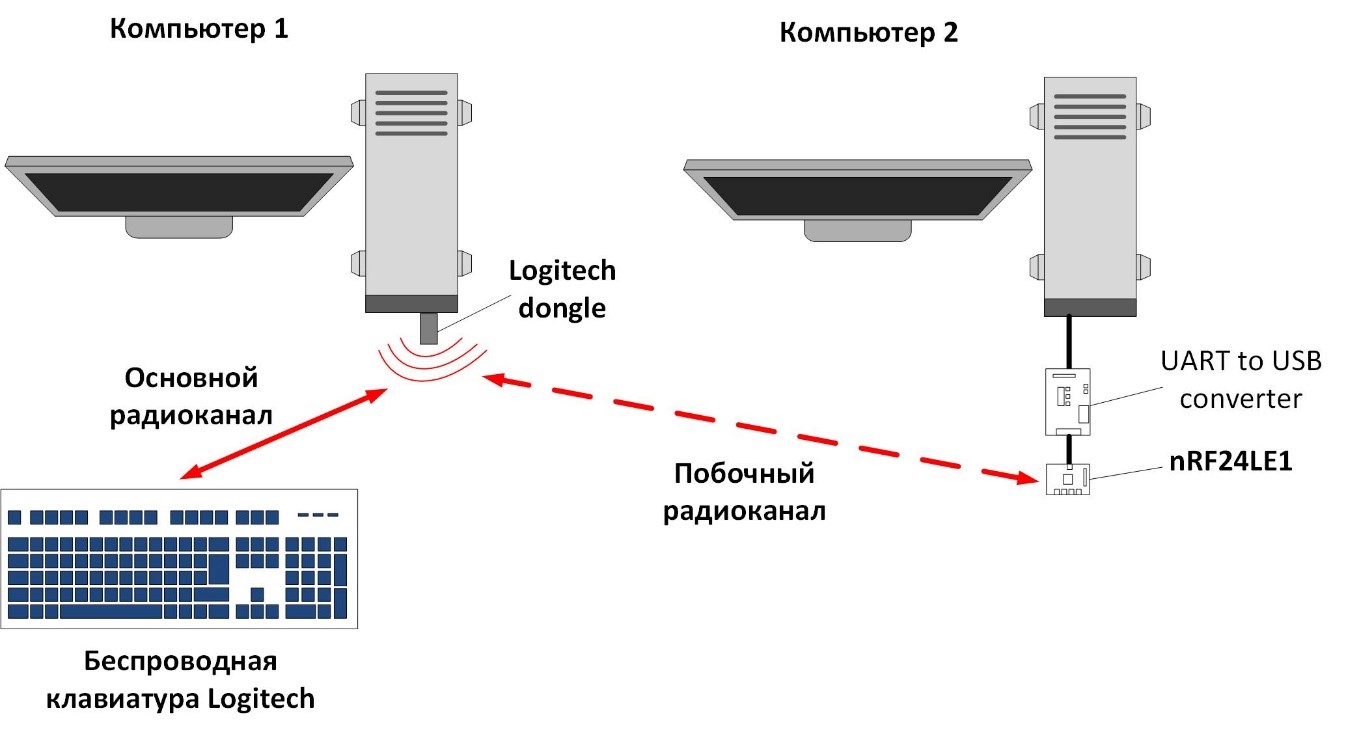
Logitech Wireless Keyboard Radio Interception Diagram

NRF24 based module
On the stand during normal keyboard operation after connecting it to the Logitech dongle, we observed the transmission of open data on keystrokes in the secondary radio channel and the normal transmission of encrypted data in the main radio interface. Thus, we were able to provide a direct interception of the user's keyboard input:
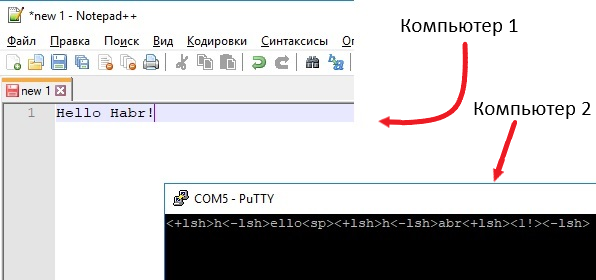
Keyboard Interception Result
The injected code introduces slight delays in the operation of the dongle firmware. However, they are too small for the user to notice.
As you can imagine, any Logitech keyboard compatible with Unifying technology can be used for such an attack vector. Since the attack is aimed at the Unifying receiver, which is included with most Logitech keyboards, it does not depend on the specific keyboard model.
Conclusion
The results of the study suggest that the attackers could use the considered scenario: if the hacker replaces the victim with a dongle receiver for the Logitech wireless keyboard, he will be able to find out the passwords for the victim's accounts with all the ensuing consequences. Do not forget that injecting keystrokes is also possible, which means that it is not difficult to execute arbitrary code on the victim’s computer.
What if an attacker can remotely modify the firmware of any Logitech dongle via USB? Then from nearby dongles you can add a network of repeaters and increase the creepage distance. Although the “financially secure” attacker has modern radio reception with highly selective systems, sensitive radios with a short frequency tuning time and narrowly oriented antennas, they will allow you to “listen” to keyboard input and press keys even from a neighboring building.
Professional radio equipment
Since the Logitech keyboard wireless data channel is fairly well protected, the attack vector found requires physical access to the receiver, which greatly limits the attacker. The only protection option in this case could be the use of cryptographic protection mechanisms for the receiver firmware, for example, checking the signature of the downloaded firmware on the receiver side. But, unfortunately, NRF24 does not support this and it is impossible to implement protection within the current device architecture. So take care of your dongles, because the described version of the attack requires physical access to them.

Raccoon Security is a special team of experts at the Volcano Scientific and Technical Center in the field of practical information security, cryptography, circuitry, reverse engineering and the creation of low-level software.