No momento, pode-se observar um ataque em larga escala pelo Wana decrypt0r 2.0 trojan-decryptor
O ataque é observado em redes diferentes, completamente sem relação entre si.

Um ransomware que se espalha no laboratório da universidade ( daqui )
Algumas empresas aconselham seus usuários a desligar seus computadores e aguardar mais instruções.

Entrando em contato com ex-colegas, fiquei surpreso com histórias semelhantes.
Quanto a mim, hoje eu estava preparando várias novas imagens do Windows para o nosso sistema em nuvem, entre elas o Windows Server 2008 R2.
O mais interessante é que, assim que instalei o Windows e configurei um endereço IP estático, ele foi imediatamente infectado por vários minutos.
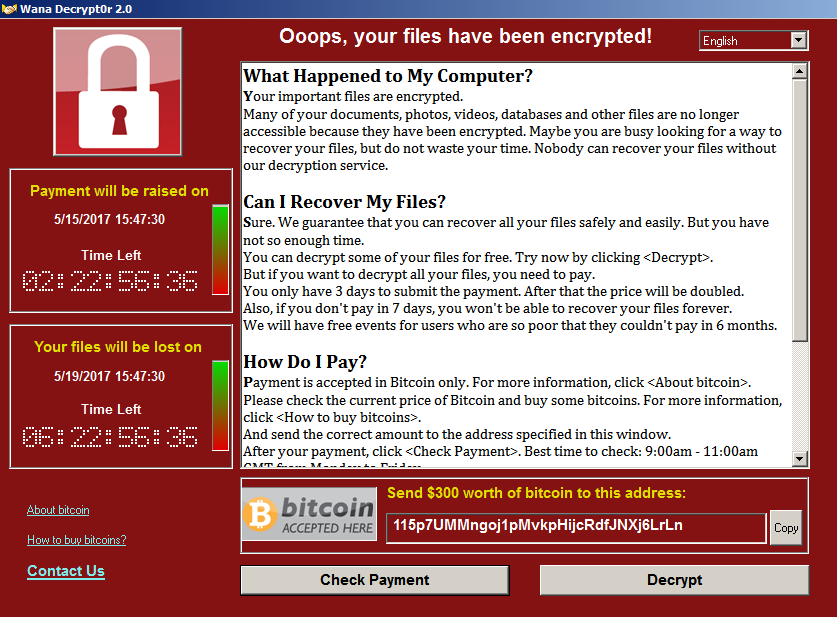
Todas as imagens do Windows foram obtidas no MSDN, os hashes correspondem e, portanto, a possibilidade de infecção da imagem é excluída.
E isso apesar do fato de que a configuração do firewall para a única interface de rede externa foi configurada como uma "rede pública".
O Nmap não encontra portas abertas . A saída nmap mostra que, mesmo nesse caso, algumas portas são abertas externamente por padrão:
Host is up (0.017s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
49154/tcp open unknown
— Virtio-, Windows CD.
ISO- — Fedora, .
Windows .
, .
:
, :
UPD: , SMBv1.
:
- , SMBv1. ( Windows 8.1 ):
dism /online /norestart /disable-feature /featurename:SMB1Protocol
UPD2: . :
100% .
, , Windows .
UPD3: :
, . FuzzBunch, Shadow Brokers Equation Group, . .
Microsoft MS 17-010, .
https://github.com/fuzzbunch/fuzzbunch .
DoublePulsar.
, 445 MS 17-010, DoublePulsar
, .
UPD4: :
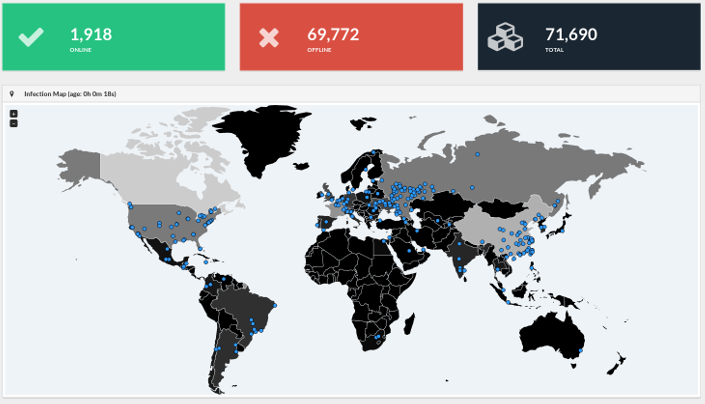
UPD5: :
UPD6: :
- WannaCrypt , iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com.
, @MalwareTechBlog, , - , .
, , , ; , . , .
- 12 . 300 . 99 , , «», . , , . .
, , Windows, .
UPD7: Microsoft (Windows XP Windows Server 2003R2)
UPD8: 2ch.hk
Shadow brokers
C/Python
Linux
?
Linux
IP
445
SMB , ,
.
UPD9: :
UPD10: killswitch UPD6.
xsash, Inflame, Pulse, nxrighthere, waisberg, forajump, Akr0n, LESHIY_ODESSA, Pentestit, alguryanow .