 本文假定读者已经了解MPLS L3VPN的基础知识。
本文假定读者已经了解MPLS L3VPN的基础知识。你好 假设您是
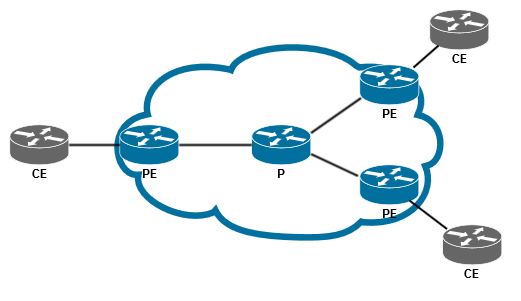
ISP 。 与任何大型ISP一样,您网络的核心是基于IP / MPLS。 如果将其完全简化,则您的网络可以由上述电路表示。 我们还假设您作为ISP,向客户出售L3VPN服务,该服务是根据RFC 4364(BGP / MPLS IP VPN)在网络上实现的。 并且,如果某个站点上的L3VPN客户端没有足够的直接连接的网络,并且想要宣布到其他站点的其他路由,那么您将在设备(PE)和客户端设备(CE)之间引发BGP会话,客户端可以通过该会话来宣布所需的路线。 有了这些,您就不会在此会话上应用任何过滤器/策略,这是因为它们是VPN客户端,并且可以随意“驱动”其中的任何内容(例如,在前缀数量的限制内)。 现在要注意的问题是:如果客户端在此BGP会话的框架内,为您(提供者)宣布路由,并向其添加路由目标社区,将会发生什么? 例如,这可能是错误或尝试的结果。
为了以防万一,我们记得路由目标是MPLS L3VPN中用于选择VRF的特殊扩展BGP社区之一,在路由表中有必要设置通过MP-BGP来的路由。 由于RT是一个社区,因此从理论上讲,没有什么可以阻止我们将其添加到常规IPv4路由中。
让我们回到如果CE在PE上宣布标有RT的路由会发生什么问题(PE上没有BGP策略)。 经过一番思考,我们可以假设有3种不同的结果:
- PE将放弃这样的公告。
- PE将从通告中删除RT,向其添加相应的VRF RT,然后将通告发送给其他PE。
- PE会原样接受公告,在其上添加相应的VRF RT(即公告中已经包含两个RT),并将公告发送给其他PE。
对于服务提供商而言,最有趣,同时又最危险的是最后一个选择。 在这种情况下,客户端可能会破坏其他VRF(客户端和内部技术)中的路由。
但是,很不错的猜测,让我们检查一下。 为了获得更大的兴趣,我们将立即在多个网络操作系统上进行检查。 在Eve-NG中,建立了以下方案:
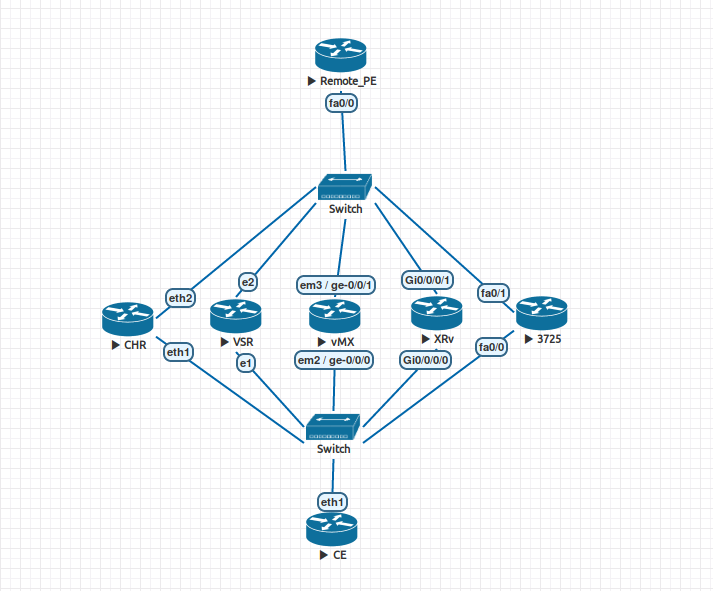
参试人员名单:
- CHR - Mikrotik CHR ,RouterOS 6.40.8
- VSR-诺基亚VSR,TiMOS 15.0.R6
- vMX -Juniper vMX,JUNOS 14.1R1.10
- XRv -Cisco XRv,IOS-XR 6.1.1
- 3725 -Cisco 3725(Dynamips),IOS 12.4
辅助路由器:
- 远程PE -Cisco 3725(Dynamips),IOS 12.4
- CE -Mikrotik CHR,RouterOS 6.40.8
电路说明:
- 测试参与者-PE路由器。 在它们各自上创建了VRF-100(RT 65001:100);在此VRF-100的框架内,组织了与CE的BGP会话,没有任何过滤器/策略。
- 每个经过测试的PE都具有与Remote_PE路由器的MP-BGP会话,并通过该会话传递VRF路由。
- CE路由器具有5个子接口(每个PE分别具有1个),在每个子接口中,BGP会话均引发到相应的CE。 每个PE都以1.1.1的形式声明其自己的前缀。 N / 32,其中N是PE从左到右的序号。 使用CE导出策略,将RT:65001:200社区添加到每个前缀中。
- 在Remote_PE上创建了两个VRF:VRF-100(RT 65001:100)和VRF-200(RT 65001:200)
- 在此省略了实际网络中通常存在的MPLS传输,P路由器,RR和其他喜悦,因为 这对我们来说都没有关系。
对于那些对“仅凭文字”的描述不满意的人,我将带来所有涉及到的设备的配置。
CE认证/interface vlan add interface=ether1 name=ether1.10 vlan-id=10 add interface=ether1 name=ether1.20 vlan-id=20 add interface=ether1 name=ether1.30 vlan-id=30 add interface=ether1 name=ether1.40 vlan-id=40 add interface=ether1 name=ether1.50 vlan-id=50 /interface wireless security-profiles set [ find default=yes ] supplicant-identity=MikroTik /routing bgp instance set default as=65002 /ip address add address=192.168.30.2/24 interface=ether1.30 network=192.168.30.0 add address=192.168.10.2/24 interface=ether1.10 network=192.168.10.0 add address=192.168.20.2/24 interface=ether1.20 network=192.168.20.0 add address=192.168.40.2/24 interface=ether1.40 network=192.168.40.0 add address=192.168.50.2/24 interface=ether1.50 network=192.168.50.0 /ip dhcp-client add disabled=no interface=ether3 add disabled=no interface=ether1.30 /ip route add distance=1 dst-address=1.1.1.1/32 type=blackhole add distance=1 dst-address=1.1.1.2/32 type=blackhole add distance=1 dst-address=1.1.1.3/32 type=blackhole add distance=1 dst-address=1.1.1.4/32 type=blackhole add distance=1 dst-address=1.1.1.5/32 type=blackhole /routing bgp network add network=1.1.1.3/32 add network=1.1.1.1/32 add network=1.1.1.2/32 add network=1.1.1.4/32 add network=1.1.1.5/32 /routing bgp peer add comment=VMX name=VMX out-filter=TO-VMX remote-address=192.168.30.1 \ remote-as=65001 add comment=CHR name=CHR out-filter=TO-CHR remote-address=192.168.10.1 \ remote-as=65001 add comment=VSR name=VSR out-filter=TO-VSR remote-address=192.168.20.1 \ remote-as=65001 add comment=XRV name=XRV out-filter=TO-XRV remote-address=192.168.40.1 \ remote-as=65001 add comment=3725 name=3725 out-filter=TO-3725 remote-address=192.168.50.1 \ remote-as=65001 /routing filter add action=accept chain=TO-VMX prefix=1.1.1.3 set-route-targets=65001:200 add action=accept chain=TO-CHR prefix=1.1.1.1 set-route-targets=65001:200 add action=accept chain=TO-VSR prefix=1.1.1.2 set-route-targets=65001:200 add action=accept chain=TO-XRV prefix=1.1.1.4 set-route-targets=65001:200 add action=accept chain=TO-3725 prefix=1.1.1.5 set-route-targets=65001:200 add action=discard chain=TO-VMX add action=discard chain=TO-CHR add action=discard chain=TO-VSR add action=discard chain=TO-XRV add action=discard chain=TO-3725 /system identity set name=CE
CHR /interface bridge add name=lo0 protocol-mode=none /interface vlan add interface=ether1 name=ether1.10 vlan-id=10 add interface=ether2 name=ether2.10 vlan-id=10 /interface wireless security-profiles set [ find default=yes ] supplicant-identity=MikroTik /routing bgp instance set default as=65001 add as=65001 name=vrf-100 redistribute-other-bgp=yes router-id=192.168.10.1 \ routing-table=VRF-100 /ip address add address=192.168.10.1/24 interface=ether1.10 network=192.168.10.0 add address=10.0.1.1/24 interface=ether2.10 network=10.0.1.0 add address=10.1.1.1 interface=lo0 network=10.1.1.1 /ip dhcp-client add disabled=no interface=ether1 /ip route vrf add export-route-targets=65001:100 import-route-targets=65001:100 interfaces=\ ether1.10 route-distinguisher=65001:100 routing-mark=VRF-100 /routing bgp instance vrf add redistribute-other-bgp=yes routing-mark=VRF-100 /routing bgp peer add address-families=vpnv4 comment=remote_PE name=remote_PE remote-address=\ 10.10.10.10 remote-as=65001 update-source=lo0 add comment=CE instance=vrf-100 name=CE remote-address=192.168.10.2 \ remote-as=65002 /routing ospf network add area=backbone network=10.0.0.0/8 /system identity set name=CHR
室速 # TiMOS-B-15.0.R6 both/x86_64 Nokia 7750 SR Copyright (c) 2000-2017 Nokia. # All rights reserved. All use subject to applicable license agreements. # Built on Mon Nov 20 12:58:19 PST 2017 by builder in /builds/150B/R6/panos/main # Generated MON JAN 01 00:32:55 2018 UTC exit all configure #-------------------------------------------------- echo "System Configuration" #-------------------------------------------------- system snmp shutdown exit time sntp shutdown exit zone UTC exit exit #-------------------------------------------------- echo "System Security Configuration" #-------------------------------------------------- system security dist-cpu-protection policy "_default-access-policy" create exit policy "_default-network-policy" create exit exit exit exit #-------------------------------------------------- echo "Log Configuration" #-------------------------------------------------- log exit #-------------------------------------------------- echo "Card Configuration" #-------------------------------------------------- card 1 card-type iom-v mda 1 mda-type m20-v no shutdown exit no shutdown exit #-------------------------------------------------- echo "Port Configuration" #-------------------------------------------------- port 1/1/1 description "CE" ethernet mode hybrid encap-type qinq exit no shutdown exit port 1/1/2 description "remote_PE" ethernet mode hybrid encap-type qinq exit no shutdown exit port 1/1/3 shutdown ethernet exit exit port 1/1/4 shutdown ethernet exit exit #-------------------------------------------------- echo "Management Router Configuration" #-------------------------------------------------- router management exit #-------------------------------------------------- echo "Router (Network Side) Configuration" #-------------------------------------------------- router Base interface "remote_PE" address 10.0.2.1/24 port 1/1/2:20.* no shutdown exit interface "system" address 10.2.2.2/32 no shutdown exit autonomous-system 65001 #-------------------------------------------------- echo "OSPFv2 Configuration" #-------------------------------------------------- ospf 0 area 0.0.0.0 interface "system" no shutdown exit interface "remote_PE" mtu 1500 no shutdown exit exit no shutdown exit exit #-------------------------------------------------- echo "Service Configuration" #-------------------------------------------------- service customer 1 create description "Default customer" exit vprn 100 customer 1 create autonomous-system 65001 route-distinguisher 65001:100 vrf-target target:65001:100 interface "CE" create address 192.168.20.1/24 sap 1/1/1:20.0 create exit exit bgp group "CE" type external export "TO-CE" peer-as 65002 neighbor 192.168.20.2 exit exit no shutdown exit service-name "VRF-100" no shutdown exit exit #-------------------------------------------------- echo "Router (Service Side) Configuration" #-------------------------------------------------- router Base #-------------------------------------------------- echo "OSPFv2 Configuration" #-------------------------------------------------- ospf 0 no shutdown exit #-------------------------------------------------- echo "Policy Configuration" #-------------------------------------------------- policy-options begin policy-statement "TO-CE" entry 10 action accept exit exit exit commit exit #-------------------------------------------------- echo "BGP Configuration" #-------------------------------------------------- bgp group "remote_PE" family vpn-ipv4 type internal local-address system neighbor 10.0.2.2 exit exit no shutdown exit exit exit all
vMX ## Last commit: 2018-05-25 12:37:27 UTC by root version 14.1R1.10; system { host-name vmx01; root-authentication { encrypted-password "$1$zA/8snt5$g3mYVmz7MzTZZOhtjRX6g1"; ## SECRET-DATA } } interfaces { ge-0/0/0 { vlan-tagging; encapsulation flexible-ethernet-services; unit 30 { vlan-id 30; family inet { address 192.168.30.1/24; } } } ge-0/0/1 { vlan-tagging; encapsulation flexible-ethernet-services; unit 30 { vlan-id 30; family inet { address 10.0.3.1/24; } } } lo0 { unit 0 { family inet { address 10.3.3.3/32; } } } } routing-options { autonomous-system 65001; } protocols { bgp { group remote_PE { type internal; local-address 10.3.3.3; family inet-vpn { unicast; } neighbor 10.10.10.10; } } ospf { area 0.0.0.0 { interface lo0.0; interface ge-0/0/1.30; } } } routing-instances { VRF-100 { instance-type vrf; interface ge-0/0/0.30; route-distinguisher 65001:100; vrf-target target:65001:100; protocols { bgp { group CE { type external; peer-as 65002; neighbor 192.168.30.2; } } } } }
Xrv !! IOS XR Configuration 6.1.1 !! Last configuration change at Fri May 25 15:24:01 2018 by Cisco ! hostname XRv vrf VRF-100 address-family ipv4 unicast import route-target 65001:100 ! export route-target 65001:100 ! ! ! interface Loopback0 no shutdown ipv4 address 10.4.4.4 255.255.255.255 ! interface MgmtEth0/0/CPU0/0 no shutdown shutdown ! interface GigabitEthernet0/0/0/0.40 no shutdown vrf VRF-100 ipv4 address 192.168.40.1 255.255.255.0 encapsulation dot1q 40 ! interface GigabitEthernet0/0/0/1.40 no shutdown ipv4 address 10.0.4.1 255.255.255.0 encapsulation dot1q 40 ! interface GigabitEthernet0/0/0/2 no shutdown shutdown ! route-policy TO-CE pass end-policy ! route-policy FROM-CE pass end-policy ! router ospf main area 0 interface Loopback0 ! interface GigabitEthernet0/0/0/1.40 ! ! ! router bgp 65001 address-family ipv4 unicast ! address-family vpnv4 unicast ! neighbor 10.10.10.10 remote-as 65001 update-source Loopback0 address-family vpnv4 unicast ! ! vrf VRF-100 rd 65001:100 bgp router-id 192.168.40.1 address-family ipv4 unicast ! neighbor 192.168.40.2 remote-as 65002 address-family ipv4 unicast route-policy FROM-CE in route-policy TO-CE out ! ! ! ! end
3725 ! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname 3725 ! boot-start-marker boot-end-marker ! ! no aaa new-model memory-size iomem 5 ip cef ! ! ! ! ip vrf VRF-100 rd 65001:100 route-target export 65001:100 route-target import 65001:100 ! no ip domain lookup ! multilink bundle-name authenticated ! ! ! archive log config hidekeys ! ! ! interface Loopback0 ip address 10.5.5.5 255.255.255.255 ! interface FastEthernet0/0 no ip address duplex auto speed auto ! interface FastEthernet0/0.50 encapsulation dot1Q 50 ip vrf forwarding VRF-100 ip address 192.168.50.1 255.255.255.0 ! interface FastEthernet0/1 no ip address duplex auto speed auto ! interface FastEthernet0/1.50 encapsulation dot1Q 50 ip address 10.0.5.1 255.255.255.0 ! router ospf 123 log-adjacency-changes network 10.0.0.0 0.255.255.255 area 0 ! router bgp 65001 no bgp default ipv4-unicast no bgp default route-target filter bgp log-neighbor-changes neighbor 10.10.10.10 remote-as 65001 neighbor 10.10.10.10 update-source Loopback0 ! address-family vpnv4 neighbor 10.10.10.10 activate neighbor 10.10.10.10 send-community extended exit-address-family ! address-family ipv4 vrf VRF-200 no synchronization exit-address-family ! address-family ipv4 vrf VRF-100 neighbor 192.168.50.2 remote-as 65002 neighbor 192.168.50.2 activate neighbor 192.168.50.2 soft-reconfiguration inbound no synchronization exit-address-family ! ip forward-protocol nd ! ! ip http server no ip http secure-server ! ! ! control-plane ! ! ! line con 0 line aux 0 line vty 0 4 ! ! end
远程PE ! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname remote_PE ! boot-start-marker boot-end-marker ! ! no aaa new-model memory-size iomem 5 ip cef ! ! ! ! ip vrf VRF-100 rd 65001:100 route-target export 65001:100 route-target import 65001:100 ! ip vrf VRF-200 rd 65001:200 route-target export 65001:200 route-target import 65001:200 ! ! multilink bundle-name authenticated ! ! ! ! archive log config hidekeys ! ! ! ! interface Loopback0 ip address 10.10.10.10 255.255.255.255 ! interface FastEthernet0/0 no ip address duplex auto speed auto ! interface FastEthernet0/0.10 description CHR encapsulation dot1Q 10 ip address 10.0.1.2 255.255.255.0 ! interface FastEthernet0/0.20 encapsulation dot1Q 20 ip address 10.0.2.2 255.255.255.0 ! interface FastEthernet0/0.30 encapsulation dot1Q 30 ip address 10.0.3.2 255.255.255.0 ! interface FastEthernet0/0.40 encapsulation dot1Q 40 ip address 10.0.4.2 255.255.255.0 ! interface FastEthernet0/0.50 encapsulation dot1Q 50 ip address 10.0.5.2 255.255.255.0 ! interface FastEthernet0/1 no ip address shutdown duplex auto speed auto ! router ospf 123 log-adjacency-changes network 10.0.0.0 0.255.255.255 area 0 ! router bgp 65001 no bgp default ipv4-unicast no bgp default route-target filter bgp log-neighbor-changes neighbor 10.1.1.1 remote-as 65001 neighbor 10.2.2.2 remote-as 65001 neighbor 10.3.3.3 remote-as 65001 neighbor 10.4.4.4 remote-as 65001 neighbor 10.5.5.5 remote-as 65001 ! address-family vpnv4 neighbor 10.1.1.1 activate neighbor 10.1.1.1 send-community extended neighbor 10.2.2.2 activate neighbor 10.2.2.2 send-community extended neighbor 10.3.3.3 activate neighbor 10.3.3.3 send-community extended neighbor 10.4.4.4 activate neighbor 10.4.4.4 send-community extended neighbor 10.5.5.5 activate neighbor 10.5.5.5 send-community extended exit-address-family ! address-family ipv4 vrf VRF-200 no synchronization exit-address-family ! address-family ipv4 vrf VRF-100 redistribute connected no synchronization exit-address-family ! ip forward-protocol nd ! ! ip http server no ip http secure-server ! ! control-plane ! ! ! line con 0 line aux 0 line vty 0 4 login ! ! end
公告CE-> PE
因此,实验很简单:使用CE,我们发布了标记为RT:65001:200的路由,在Remote-PE上,我们希望查看这些路由是否出现在路由表VRF-200中。
首先,检查VRF-100路由表:
remote_PE#show ip route vrf VRF-100 1.1.1.0 255.255.255.0 longer-prefixes Routing Table: VRF-100 Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set 1.0.0.0/32 is subnetted, 5 subnets B 1.1.1.1 [200/0] via 10.1.1.1, 00:01:02 B 1.1.1.3 [200/0] via 10.3.3.3, 05:19:08 B 1.1.1.2 [200/0] via 10.2.2.2, 00:02:47 B 1.1.1.5 [200/0] via 10.5.5.5, 01:36:05 B 1.1.1.4 [200/0] via 10.4.4.4, 02:32:21 remote_PE#
我们收到了来自所有5个PE的路线。 现在,检查以下路由是否在VRF-200中:
remote_PE#show ip route vrf VRF-200 Routing Table: VRF-200 Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set 1.0.0.0/32 is subnetted, 3 subnets B 1.1.1.1 [200/0] via 10.1.1.1, 00:01:24 B 1.1.1.3 [200/0] via 10.3.3.3, 05:19:29 B 1.1.1.2 [200/0] via 10.2.2.2, 00:03:08 remote_PE#
来自CHR,vMX和VSR的路由在VRF-200中结束。 这意味着这些PE保存了添加到CE的RT:65001:200社区。
同时,从XRv和3725开始的路由仅在VRF-100中可用。 这意味着cisco路由器从公告中删除了RT:65001:200社区。
公告PE-> CE
我们不会在那儿停下来,并检查公告在相反方向上的行为,即 从PE到CE。 我们将略微修改现有配置。
在Remote_PE上,创建一个回
送,其地址
100.100.100.100/32将由另一个PE宣布:
interface Loopback100 ip vrf forwarding VRF-100 ip address 100.100.100.100 255.255.255.255 ! router bgp 65001 address-family ipv4 vrf VRF-100 redistribute connected exit-address-family !
在vMX上,请记住我们没有配置MPLS传输,这意味着inet.3表为空,并且来自Remote_PE的路由将被隐藏。 将OSPF路由复制到inet.3。
set routing-options rib-groups RG-INET3 import-rib [ inet.0 inet.3 ] set protocols ospf rib-group RG-INET3
在其余路由器上,当前设置应该足够了。
我们看一下CE上的路线:
[admin@CE] > ip route print detail where dst-address=100.100.100.100/32 Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme, B - blackhole, U - unreachable, P - prohibit 0 ADb dst-address=100.100.100.100/32 gateway=192.168.20.1 gateway-status=192.168.20.1 reachable via ether1.20 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=VSR 1 Db dst-address=100.100.100.100/32 gateway=192.168.50.1 gateway-status=192.168.50.1 reachable via ether1.50 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete received-from=3725 2 Db dst-address=100.100.100.100/32 gateway=192.168.10.1 gateway-status=192.168.10.1 reachable via ether1.10 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=CHR 3 Db dst-address=100.100.100.100/32 gateway=192.168.30.1 gateway-status=192.168.30.1 reachable via ether1.30 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=VMX 4 Db dst-address=100.100.100.100/32 gateway=192.168.40.1 gateway-status=192.168.40.1 reachable via ether1.40 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete received-from=XRV
除思科外,所有路由器均在路由声明中离开了路由目标。 思科之所以这样做,并不是因为默认情况下向其发送了任何社区信息。 修复它。
3725:*
router bgp 65001 address-family ipv4 vrf VRF-100 neighbor 192.168.50.2 send-community extended
XRv:*
router bgp 65001 vrf VRF-100 neighbor 192.168.40.2 address-family ipv4 unicast send-extended-community-ebgp
*使用这些命令不会以CE-> PE公告的任何方式更改第一个实验的结果。现在再次查看CE上的路由:
[admin@CE] > ip route print detail where dst-address=100.100.100.100/32 Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme, B - blackhole, U - unreachable, P - prohibit 0 ADb dst-address=100.100.100.100/32 gateway=192.168.20.1 gateway-status=192.168.20.1 reachable via ether1.20 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=VSR 1 Db dst-address=100.100.100.100/32 gateway=192.168.50.1 gateway-status=192.168.50.1 reachable via ether1.50 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=3725 2 Db dst-address=100.100.100.100/32 gateway=192.168.10.1 gateway-status=192.168.10.1 reachable via ether1.10 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=CHR 3 Db dst-address=100.100.100.100/32 gateway=192.168.30.1 gateway-status=192.168.30.1 reachable via ether1.30 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=VMX 4 Db dst-address=100.100.100.100/32 gateway=192.168.40.1 gateway-status=192.168.40.1 reachable via ether1.40 distance=20 scope=40 target-scope=10 bgp-as-path="65001" bgp-origin=incomplete bgp-ext-communities="RT:65001:100" received-from=XRV
现在,绝对所有的PE都向CE发送带有RT指示的路由。
就我个人而言,类似的结果似乎有些奇怪。 虽然从理论上讲可以在CE-> PE公告中保留RT,但在PE-> CE公告中,RT显然是不必要的信息。
此外,针对CE-> PE以及针对PE-> CE的RT守恒现象的存在可能对AS跨选项A产生负面影响。
标题“ RFC告诉我们的内容”
本文开头提到的
RFC 4364特别声明了这一点:
如果PE和CE本身是BGP对等体,则
SP可以允许客户在限制范围内指定其
路线将被分配。 SP和客户将需要
事先商定允许附加的RT集合
客户的VPN路由。 然后,CE可以附加一个或多个
分配给PE的每个IP路由的RT。 这给
客户在约定的时间内可以自由进行实时指定
限制,其路线分配政策。 如果允许CE
将RT附加到其路由上,PE必须过滤掉所有
包含不允许客户使用的RT。 如果CE是
不允许将RT附加到其路由,但无论如何这样做,PE
必须先删除RT,然后再将客户的路由转换为VPN-
IPv4路由。
因此,在CE-> PE公告中保留RT具有完全的法律依据,尽管在我看来这的实际应用似乎有些可疑。
关于RT在RFC中的公告PE-> CE,什么也没说。
从与CE的会话中删除RT
思科事先已明确一切。 在CE-> PE公告中,所有RT均被分类删除(我找不到能改变此行为的命令),在PE-> CE公告中,默认情况下不存在RT,这足以不发送扩展的社区。
我们将弄清楚如何消除测试中其他参与者的RT。
杜松
从公告(PE-> CE和CE-> PE)中删除RT所需要做的就是创建策略,并删除以“ target:”开头的所有社区,这是第一个术语,并以按照以下术语进行处理。
例如,如果我们要接受并宣布所有路线,只需从它们中删除RT:
edit policy-options set community RT-ALL members target:.+:.+ set policy-statement TO-CE term 10 then community delete RT-ALL set policy-statement TO-CE term 10 then next term set policy-statement TO-CE then accept copy policy-statement TO-CE to policy-statement FROM-CE
诺基亚手机
要禁用将扩展团体发送到BGP对等体,可以使用以下命令:
configure service vprn "VRF-100" bgp group "CE" disable-communities extended
为了从CE公告中删除RT,您需要创建一个与在Juniper中类似的策略,并将其应用于与CE的会话中。
configure router policy-options begin community "RT-ALL" members "target:.+&.+" policy-statement FROM-CE entry 10 action next-entry community remove "RT-ALL" exit exit default-action accept exit exit commit
米克罗蒂克
但是有了Mikrotik,我们将感到失望。 根本没有机制可以从公告中删除RT。 似乎在路由筛选器中有一个set-route-targets参数,并且会执行类似的操作
/routing filter add chain=TO-CE set-route-targets="" action=passthrough add chain=TO-CE action=accept
但是,不幸的是,set-route-targets =“”表示必须从规则中完全删除此参数(set-route-targets)。 一个例子:
[admin@CE] /routing filter> add chain=TO-CE action=passthrough set-route-targets="" [admin@CE /routing filter> print where chain=TO-CE Flags: X - disabled 0 chain=TO-CE invert-match=no action=passthrough set-bgp-prepend-path=""
在这种情况下,仍然值得记住的是,Mikrotik主要是一种先进的SOHO路由器,可能要求运营商级路由器提供相同的功能可能并不正确。 它仍然依赖于RouterOS 7。
结论
将所需的RT添加到公告中,您的客户端仍将无法访问MGMT VRF,例如,因为 连接将是单向的。 但是,客户端很有可能中断MGMT VRF中的路由(当然,为此,您需要猜测RT和已宣布的路由)。
另外,在实施跨域选项A时,来自提供商A的路由可能会进入提供商B的网络,并保留其RT。 此外,如果在提供商B的网络中此RT已经在其他某个VRF下使用,则路由会泄漏到该VRF中,这当然不是所希望的行为。
因此,该问题不太严重,因为 为了让她“射击”,必须同时考虑几个因素。 另一方面,纠正这种有害行为要比弄清楚为什么突然“不起作用”要容易得多。
同样,非常简短:
1.如果可能,请从PE和CE之间的公告中删除RT(当然,除非您需要它们)。
2.从测试结果来看,cisco-PE的拥有者可以安然入睡,其RT被切断在机器上。 但是,以防万一,我会仔细检查。 也许在其他版本的iOS中,行为是不同的。