我们想与1cloud服务器分享我们的经验。 我们不想怪任何人,我们只是想将问题公开显示,以便1cloud员工有动力对这个问题进行详细的分析。
一切始于最近几个月,在Windows服务器1cloud上,我们开始注意到负载异常,但并没有对其施加太多重视,因为Windows服务器主要用于执行各种小任务,例如使用浏览器和任何其他程序,尤其是人们希望找出那里的东西以及如何。
但是前几天,1cloud员工遇到了非常不愉快和侮辱性的情况,这促使我们发布了这篇文章。 我们一直在使用1cloud服务器1.5至2年,我们没有违反使用服务器的规则。 当我登录到自己的帐户并看到“我们的服务器已被管理员阻止”字样被阻止时,我感到非常惊讶。 阻止的原因:蛮力。
我将写信给支持人员,并从技术支持服务中看到一条新消息,消息中说:
你好
您的IP 111.111.11.111服务器记录了异常的网络活动:尝试连接到端口22(SSH)上的大量任意服务器
服务器可能已被黑客入侵。 您需要快速解决问题。
如果对此请求没有反应,则服务器将与网络断开连接。
由于员工错误或服务器管理系统出现问题,所有40台服务器均关闭,而不是出现一个问题,并且一天之内都不可用。 支持人员收到以下消息:
服务器已解锁,它们将自动打开。 根据内部说明,将断开一台问题服务器的连接,将对此事件进行调查。
为了避免这种情况,请更迅速地响应治疗。
另外,请报告消除服务器问题的方法。
这当然是一种不愉快的情况,但是我认为这确实发生了,我们开始解决导致服务器阻塞的问题。 服务器没有按照我们的承诺自动打开,我不得不手动启动所有服务器,但是与主要问题相比,这是一件小事。 登录服务器,立即注意到我们8月20日最后一次通过ssh连接的奇怪事件,各种恶意文件分别在21日和22日上传到服务器。 事实证明,在1cloud上创建每个服务器的过程中,添加了一些可疑用户“用户”,该用户的文件夹中将来会出现一堆恶意文件,其中包括xrig矿机。
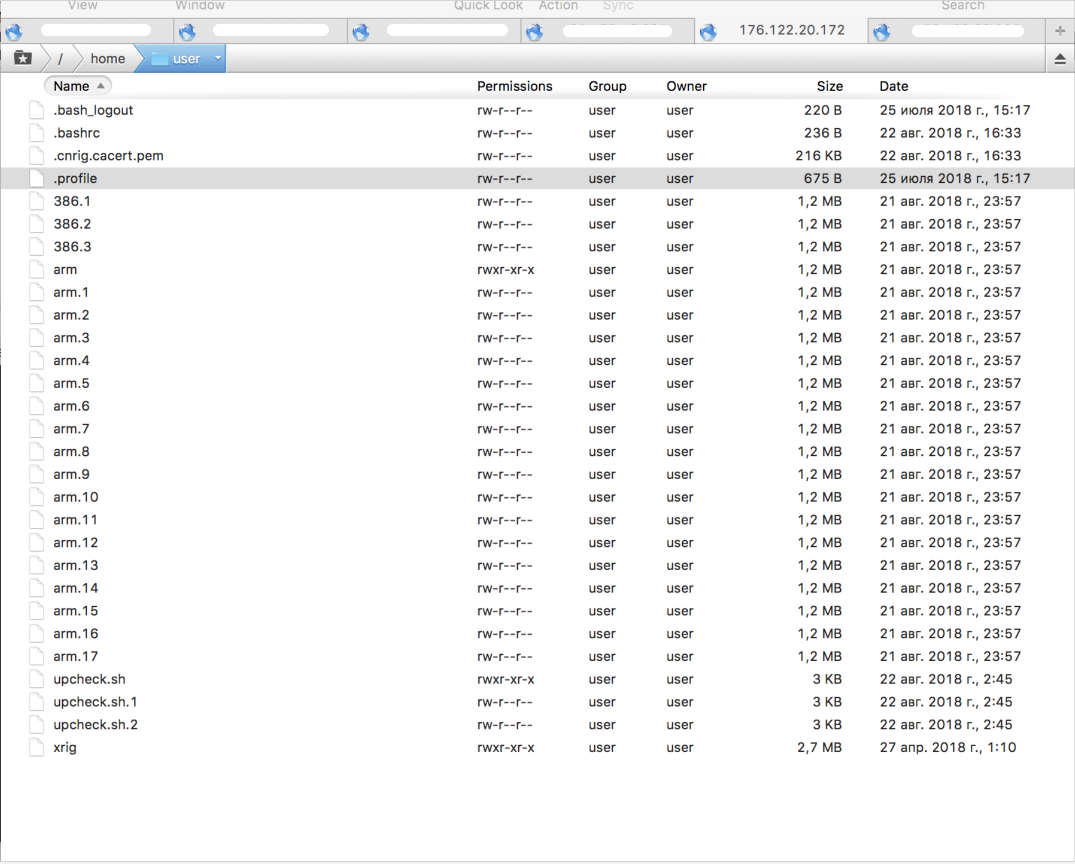
他们开始致电支持人员,解释情况,询问创建服务器时添加了什么样的用户“用户”以及在其文件夹中创建了哪些恶意文件。 技术支持人员试图否认在创建服务器时自动添加了用户“用户”,并声称他们与此无关。 我们为测试创建了一个新服务器,用户“用户”也立即出现在该服务器上,但到目前为止还没有恶意文件,因为恶意软件不是立即(而是一天或更长时间)注入服务器的。 在默认情况下,用户“用户”出现在新创建的服务器上的位置,技术支持人员无法给出明确的答案。
他们爬过去查看日志,结果发现有人知道密码并连接到用户“用户”,并将恶意文件上传到服务器进行挖掘和暴力破解。 我想立即澄清一下,没有向用户提供1cloud客户端的密码,而且,技术支持人员顽固地对我说,即使这样的用户不在他们的服务器上,也从来没有,尽管我们在整个期间都看到这样的用户在所有服务器上使用服务器。
我们相信,一切都表明1cloud的一名员工(我真的希望这不是指南)开始暗中寻觅,在其客户的服务器上安装矿工和恶意软件,我们为此支付了费用。 创建服务器后的最初几天,有人通过用户“用户”连接到该服务器,同时知道他的密码,并控制了您的服务器。 您说这也许是蛮横的,但是不幸的是,没有,日志显示它不是蛮横的,即没有密码选择的普通授权。 在以“用户”用户身份进入服务器之前,日志显示尝试连接到用户user,admin,ubuntu,ubnt,test和osmc一次,然后使用用户“ user”成功登录。
Aug 20 03:46:59 debian8x64 sshd[1328]: Invalid user test from 219.135.136.144
Aug 20 03:46:59 debian8x64 sshd[1328]: input_userauth_request: invalid user test [preauth]
Aug 20 03:46:59 debian8x64 sshd[1328]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:46:59 debian8x64 sshd[1328]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:02 debian8x64 sshd[1328]: Failed password for invalid user test from 219.135.136.144 port 1072 ssh2
Aug 20 03:47:02 debian8x64 sshd[1328]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:03 debian8x64 sshd[1330]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:03 debian8x64 sshd[1330]: Invalid user debian from 219.135.136.144
Aug 20 03:47:03 debian8x64 sshd[1330]: input_userauth_request: invalid user debian [preauth]
Aug 20 03:47:03 debian8x64 sshd[1330]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:47:03 debian8x64 sshd[1330]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:05 debian8x64 sshd[1330]: Failed password for invalid user debian from 219.135.136.144 port 8178 ssh2
Aug 20 03:47:05 debian8x64 sshd[1330]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:06 debian8x64 sshd[1332]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:07 debian8x64 sshd[1332]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144 user=root
Aug 20 03:47:09 debian8x64 sshd[1332]: Failed password for root from 219.135.136.144 port 14224 ssh2
Aug 20 03:47:09 debian8x64 sshd[1332]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:10 debian8x64 sshd[1334]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:10 debian8x64 sshd[1334]: Invalid user debian from 219.135.136.144
Aug 20 03:47:10 debian8x64 sshd[1334]: input_userauth_request: invalid user debian [preauth]
Aug 20 03:47:11 debian8x64 sshd[1334]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:47:11 debian8x64 sshd[1334]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:13 debian8x64 sshd[1334]: Failed password for invalid user debian from 219.135.136.144 port 21466 ssh2
Aug 20 03:47:13 debian8x64 sshd[1334]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:15 debian8x64 sshd[1336]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:15 debian8x64 sshd[1336]: Invalid user osmc from 219.135.136.144
Aug 20 03:47:15 debian8x64 sshd[1336]: input_userauth_request: invalid user osmc [preauth]
Aug 20 03:47:15 debian8x64 sshd[1336]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:47:15 debian8x64 sshd[1336]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:16 debian8x64 sshd[1336]: Failed password for invalid user osmc from 219.135.136.144 port 28516 ssh2
Aug 20 03:47:17 debian8x64 sshd[1336]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:18 debian8x64 sshd[1338]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:18 debian8x64 sshd[1338]: Invalid user ubnt from 219.135.136.144
Aug 20 03:47:18 debian8x64 sshd[1338]: input_userauth_request: invalid user ubnt [preauth]
Aug 20 03:47:18 debian8x64 sshd[1338]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:47:18 debian8x64 sshd[1338]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:20 debian8x64 sshd[1338]: Failed password for invalid user ubnt from 219.135.136.144 port 34656 ssh2
Aug 20 03:47:20 debian8x64 sshd[1338]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:22 debian8x64 sshd[1340]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:22 debian8x64 sshd[1340]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144 user=root
Aug 20 03:47:24 debian8x64 sshd[1340]: Failed password for root from 219.135.136.144 port 40882 ssh2
Aug 20 03:47:24 debian8x64 sshd[1340]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:25 debian8x64 sshd[1342]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:25 debian8x64 sshd[1342]: Invalid user admin from 219.135.136.144
Aug 20 03:47:25 debian8x64 sshd[1342]: input_userauth_request: invalid user admin [preauth]
Aug 20 03:47:26 debian8x64 sshd[1342]: Failed none for invalid user admin from 219.135.136.144 port 47736 ssh2
Aug 20 03:47:26 debian8x64 sshd[1342]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:27 debian8x64 sshd[1344]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:27 debian8x64 sshd[1344]: Invalid user test from 219.135.136.144
Aug 20 03:47:27 debian8x64 sshd[1344]: input_userauth_request: invalid user test [preauth]
Aug 20 03:47:27 debian8x64 sshd[1344]: pam_unix(sshd:auth): check pass; user unknown
Aug 20 03:47:27 debian8x64 sshd[1344]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=219.135.136.144
Aug 20 03:47:29 debian8x64 sshd[1344]: Failed password for invalid user test from 219.135.136.144 port 50546 ssh2
Aug 20 03:47:29 debian8x64 sshd[1344]: Connection closed by 219.135.136.144 [preauth]
Aug 20 03:47:30 debian8x64 sshd[1346]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:31 debian8x64 sshd[1346]: Accepted password for user from 219.135.136.144 port 56492 ssh2
Aug 20 03:47:31 debian8x64 sshd[1346]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:33 debian8x64 sshd[1350]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:33 debian8x64 sshd[1350]: Accepted password for user from 219.135.136.144 port 60134 ssh2
Aug 20 03:47:33 debian8x64 sshd[1350]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:35 debian8x64 sshd[1354]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:35 debian8x64 sshd[1354]: Accepted password for user from 219.135.136.144 port 4485 ssh2
Aug 20 03:47:35 debian8x64 sshd[1354]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:38 debian8x64 sshd[1358]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:38 debian8x64 sshd[1358]: Accepted password for user from 219.135.136.144 port 9509 ssh2
Aug 20 03:47:38 debian8x64 sshd[1358]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:42 debian8x64 sshd[1362]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:42 debian8x64 sshd[1362]: Accepted password for user from 219.135.136.144 port 15833 ssh2
Aug 20 03:47:42 debian8x64 sshd[1362]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:43 debian8x64 sshd[1346]: pam_unix(sshd:session): session closed for user user
Aug 20 03:47:44 debian8x64 sshd[1366]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:44 debian8x64 sshd[1366]: Accepted password for user from 219.135.136.144 port 19619 ssh2
Aug 20 03:47:44 debian8x64 sshd[1366]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:46 debian8x64 sshd[1370]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:46 debian8x64 sshd[1370]: Accepted password for user from 219.135.136.144 port 23935 ssh2
Aug 20 03:47:46 debian8x64 sshd[1370]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:48 debian8x64 sshd[1374]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:49 debian8x64 sshd[1374]: Accepted password for user from 219.135.136.144 port 28277 ssh2
Aug 20 03:47:49 debian8x64 sshd[1374]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:51 debian8x64 sshd[1378]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:51 debian8x64 sshd[1378]: Accepted password for user from 219.135.136.144 port 31735 ssh2
Aug 20 03:47:51 debian8x64 sshd[1378]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:53 debian8x64 sshd[1383]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:53 debian8x64 sshd[1383]: Accepted password for user from 219.135.136.144 port 36097 ssh2
Aug 20 03:47:53 debian8x64 sshd[1383]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:47:55 debian8x64 sshd[1388]: reverse mapping checking getaddrinfo for 144.136.135.219.broad.gz.gd.dynamic.163data.com.cn [219.135.136.144] failed - POSSIBLE BREAK-IN ATTEMPT!
Aug 20 03:47:56 debian8x64 sshd[1388]: Accepted password for user from 219.135.136.144 port 39885 ssh2
Aug 20 03:47:56 debian8x64 sshd[1388]: pam_unix(sshd:session): session opened for user user by (uid=0)
Aug 20 03:48:16 debian8x64 sshd[1350]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:19 debian8x64 sshd[1354]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:22 debian8x64 sshd[1358]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:25 debian8x64 sshd[1362]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:27 debian8x64 sshd[1366]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:29 debian8x64 sshd[1370]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:31 debian8x64 sshd[1374]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:34 debian8x64 sshd[1378]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:36 debian8x64 sshd[1383]: pam_unix(sshd:session): session closed for user user
Aug 20 03:48:38 debian8x64 sshd[1388]: pam_unix(sshd:session): session closed for user user由此只能得出一个结论:如今,使用1cloud服务器来托管任何重要项目并不安全,因为您的数据可能会由于某些麻烦进入1cloud而丢失,从而在操作系统模板中留下了漏洞。 目前,我们设法发现Debian 8模板中确实存在此漏洞,让1cloud员工自己检查其余漏洞,我们已经做了足够的工作来告知他们此漏洞。
与1cloud进行了长时间的电话交谈后,我们无法对发生的事情有一个清晰的解释。 我们很不情愿地向我们道歉,并说他们应该一旦替换掉操作系统模板就将其排除在外,并从中排除所有不必要的模板。 有人问这个问题,伙计们,您还需要从OS模板中删除什么? 您不关心您的客户吗? 您如何出售与数千名在这些服务器上存储TB的重要数据的客户类似的违规服务器? 只有一个结论-云只会升值利润;客户数据对他们来说毫无价值! 1cloud的家伙,如果您认为我错了,请向我证明相反的意思!
亲爱的1cloud员工,如果您有任何疑问,我们欢迎您进行交流-写票。 我们已经准备好讨论这种情况,但是只能与有能力的人员进行讨论,而不能与支持人员进行顽强地尝试向我们证明在创建服务器时不添加任何名称为“ user”的用户。 我们还准备提供所有必要的数据,以帮助彻底结束易受攻击的1cloud服务器的销售!