 OTRS
OTRS是用Perl编写的开源票务请求系统。
有两种选择:
我将列出该系统支持的一些
功能 :
- ITSM模块(服务级别管理,变更管理,配置管理,CMDB)
- 响应式Web界面
- API
- SLA和服务
- 多租户
- 升级
- 身份验证:DB,LDAP,HTTPBasicAuth,Radius
- 支持MySQL,MariaDB,PostgreSQL,Oracle
而且,如果您发现其中的缺陷,那是不寻常的界面,并且设置起来很复杂。 重点介绍了使用各种LDAP目录进行授权(组,RBAC,对多家客户公司的支持),身份验证和元数据同步(名称,电话等)的基础知识
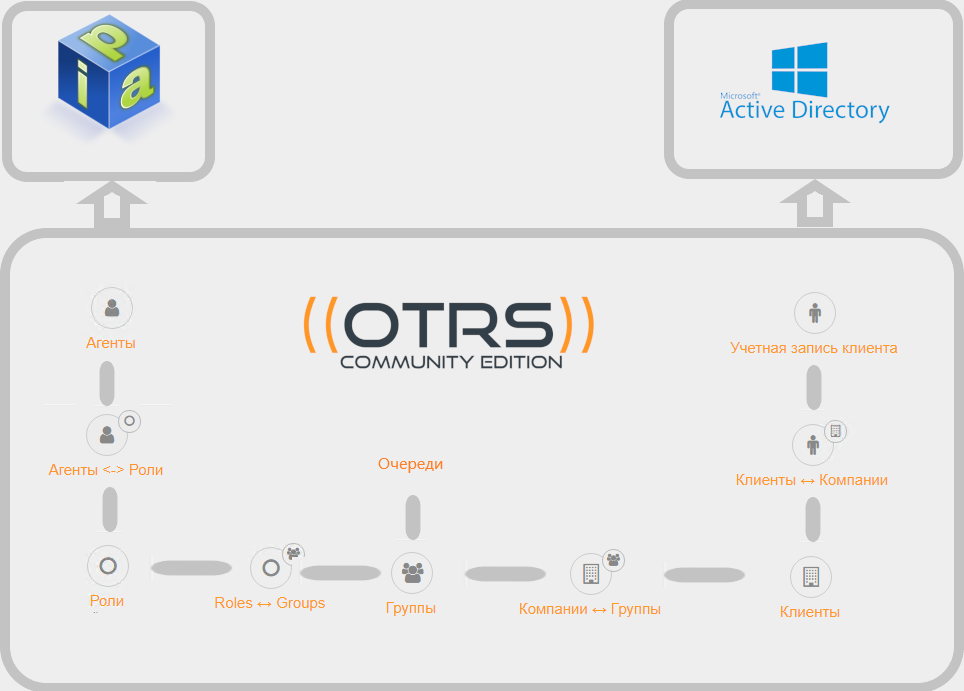
客户端,队列,代理和组
安装OTRS之后,您将立即可以访问:
- 客户 -可以通过发送信件或使用Web访问来创建应用程序
- 队列 -每个应用程序属于其中一个应用程序队列
- 代理 -从他们可用的队列中从事应用程序执行的IT专业人员
- 组 -连接队列,客户端和代理以及设置代理权限的实体-例如,只读,更改应用程序的优先级等。

标准组
安装系统后,您将看到三个创建的组:
- 管理员 -组成员可以管理(配置)OTRS
- 统计 -自定义和运行报告的能力
- 用户 -客户端,队列和代理的标准组
集团相关权利
基本权利
可以在限制代理程序操作的组中配置的主要权限:
- 该组/队列中应用程序中的只读权限
- move-将请求移至该组/队列的权限
- 创建 -在此组/队列中创建应用程序的权限
- note-向该组/队列中的应用程序添加注释的权限
- owner-更改此组/队列中应用程序所有者的权限
- 优先级 -更改此组/队列中应用程序优先级的权限
- 读取/写入 -对该组/队列中的请求具有完全的读取和写入权限
附加权利
还具有其他权限,可以在设置(系统::权限)中启用其显示:
- 报告 -提供对报告页面的访问
- redirect-重定向/退回邮件消息的权利(ticketZoom中的重定向/退回链接)
- 创建 -有权对申请做出回应
- 客户 -更改此应用程序的客户的权利
- forward-转发消息的权利(使用“转发”按钮)
- 待定 -转移待定申请的权利
- 电话 -以消息/便笺的形式将客户通话内容添加到应用程序的权利
- 负责人 -更改负责申请者的权利
更详细地考虑这一点:
- 每个客户端可以包含在一个或几个组中,最初所有客户端都是用户组的成员
- 每个订单队列都与任何一个组相关联
- 通过Web界面,客户端可以在队列中发出请求,这些队列中包括他的组可以访问
- 当客户通过电子邮件发送请求时,可以根据对信件属性(例如,发件人的地址或信件标题)的分析来更改应用程序的特性,包括应用程序将要进入的队列
- 如果客户端通过电话呼叫,则代理可以通过选择代理可用的任何队列来手动创建应用程序
- 希望客户端的应用程序始终处于客户端可用的队列中,否则他将无法通过Web界面访问该应用程序
- 代理可以根据应用程序所在队列的权限在应用程序中执行操作

数据库认证
身份验证和授权代理和客户端的标准方法是通过数据库。
例如,使用数据库设置代理身份验证如下所示:
$Self->{'AuthModule'} = 'Kernel::System::Auth::DB';
客户:
$Self->{'Customer::AuthModule'} = 'Kernel::System::CustomerAuth::DB'; $Self->{'Customer::AuthModule::DB::Table'} = 'customer_user'; $Self->{'Customer::AuthModule::DB::CustomerKey'} = 'login'; $Self->{'Customer::AuthModule::DB::CustomerPassword'} = 'pw';
我们还将保留此身份验证方法,并通过LDAP添加身份验证。
角色和公司
我们还将通过添加角色和公司来扩展授权功能:
- 角色 -通过连接组和代理允许更灵活的访问控制
- 公司 -允许隔离各种客户的应用程序(无论是不同部门还是公司)
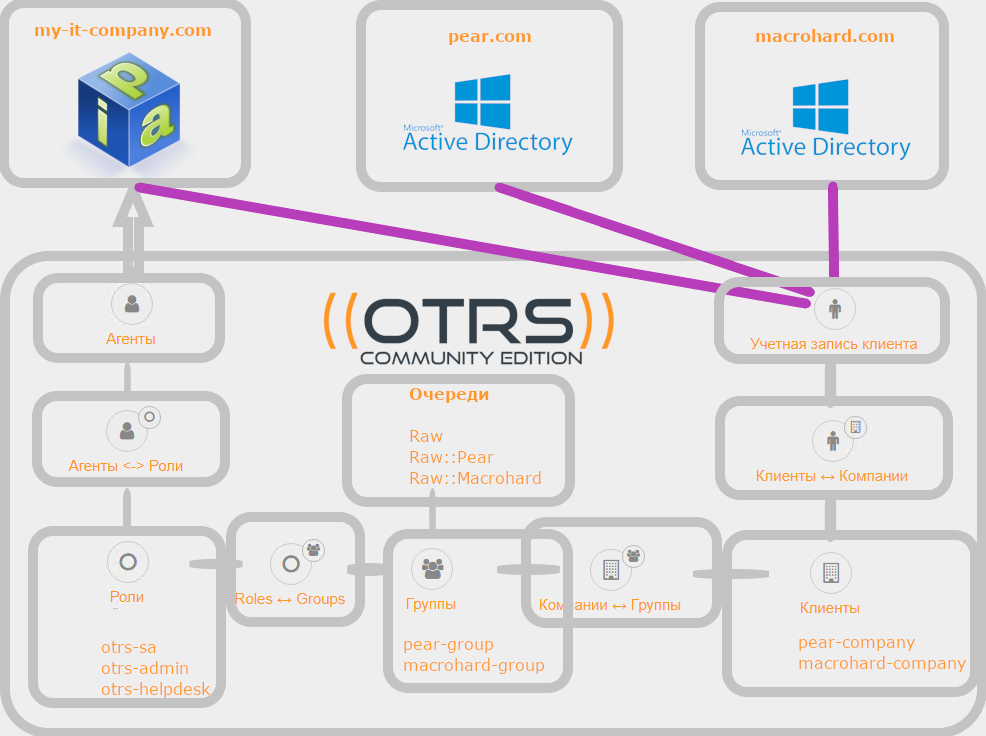
问题陈述
您是my-it-company.com上OTRS系统的管理员,该公司向其他公司(或您所拥有的单位)提供服务。
您确实不希望手动创建新的代理和客户帐户,也不希望填写其他信息,例如电子邮件地址,电话号码,职位,地址和内阁编号-毕竟,这已经在LDAP目录中。
您的公司还将获得明显的优势-在所有系统中使用单个员工密码,在LDAP中阻止帐户将阻止对所有其他服务的访问。
my-it-company.com在Linux上运行,并使用Red Hat FreeIPA作为目录服务器,您所服务的部门使用各种Microsoft Active Directory林,您没有该林具有联合身份,但可以连接到域控制器。
您需要将应用程序流与不同的客户端分开,并实现对队列的不同级别的代理访问权限-管理者应该能够更改系统中任务的优先级。
您公司的员工还可以根据
my-it-company.com的内部需求在系统中设置任务,有时既是代理商又是客户(有时不是同时)。
准备工作
查看LDAP的帐户
如果禁止匿名浏览目录树,我们将在具有足够权限进行LDAP查询的域名
my-it-company.com ,
pear.com和
macrohard.com中创建帐户(我们称它们为ldap-bot)
FreeIPA组与OTRS角色同步
我们将在FreeIPA上创建三组用户,这三组用户将与我们的OTRS角色同步,例如:
- otrs-sa-该组的成员将有权访问OTRS管理,但我们不会授予对队列的访问权限,因此我们不想一直在管理员的领导下工作),
- otrs-admins-我们的经理有权更改应用程序的优先级)和
- otrs-服务台 -我们的专家帐户
公司属性
选择我们用来确定与公司的隶属关系的属性。 使其成为“组织”属性。 例如,从组织和技术角度讲,一切都变得如此,并且所有域中的所有用户始终在“组织”字段中具有值:
- 我的公司 -适用于my-it-company.com的员工
- 梨公司 -针对pear.com的员工
- macrohard-company-适用于macrohard.com的员工
定义FreeIPA使用的用户属性
我们研究FreeIPA方案,找出同步所需的属性名称(名称,登录名,电话等)。
kinit laptevs ipa user-show --all --raw laptevs
我们得出类似的结论:dn:uid = laptevs,cn =用户,cn =帐户,dc =我的公司,dc = com
uid:laptevs
别名:斯坦尼斯拉夫
sn:拉普捷夫
cn:Laptev Stanislav
首字母缩写:SL
主目录:/ home / laptevs
gecos:拉普捷夫·斯坦尼斯拉夫
loginshell:/ bin / sh
krbcanonicalname:laptevs@MY-IT-COMPANY.COM
krbprincipalname:laptevs@MY-IT-COMPANY.COM
邮件:laptevs@MY-IT-COMPANY.COM
uidnumber:1344600003
gidnumber:1344600003
l:莫斯科
电话号码:+7(863)999-99-99
手机:+7(999)999-99-99
ou:我的公司
标题:SysAdm
sshpubkeyfp:SHA256:Yi8mKF + j28 / r2cpxLgIbvZ / Oymt57rhliHKhqBuJxqE laptevs-putty(ssh-rsa)
nsaccountlock:否
has_password:TRUE
has_keytab:TRUE
displayName:Laptev Stanislav
ipaSshPubKey:c3NoLXJzYSBBQUFBQjNOemFDMXljMkVBQUFBQkpRQUFBZ0VBNjQ1RTJjSjIvWXVVYm9GNzdZY3hLNzBndm1jWlgrZjBZTVpsaXRQVXNCWFZ0cENtTEtwcjRwK2JEeUdhRzNLTWx1T08ydW9wS0pXRk9mWE83Zzl3OTYzdklQblN3MzVHSmI3VGhhbk1pTXpNUE82T1lQZEY0em14b2k4N 0RGYkdXV2V6aGwzcitsbmFGYTB0dEQ5TkFWRU1Fb3BMdmkzcHZ1UXpyVmNjVlMxamFxY1dNT2ZGUC9TRlVoY1dGeVpZd3Z6eW0wWnZObUZtdjVjVHJGNzJMSXZOdHlsNkZGK2ZaU3ZpS01mcXZ6NStkT2xZZGd5bVVSOG5iaVpkTXZKaTIvbzhjTy84ekpoMFhtSnVRSjJXNEVvYVEvajVTTm8ySjZ6NklXNk I3cFB4Y002a0tJcUp5N08zTkNOcGRrVmVQbEFHbThsOFZDREpVa1RLSjRGOS9mSTZFUkhxVUZwK3p1VENTR1R3ZWlKdXppenFSZWJTTkNiMXh3RldmUitvYzFLdWNZSU5QbTYxRi93YXhOcC9aSG9OK2w1dCtkYWI4cElZSGZzTnNUNWx2RWt4Ukh0bnNyeUxsbWk1ZVdzd3RBbDB3TUpWd1cvUWNJcjhOaVN Ybm96Q3dHWTZCaTQ2L0FGTGVidmFLV0tKRmpKZFgxOFlRVDRpVzZGaE83aW40TGlUamlNaENXbStvbjNQbERYeXZpdkJ1WkFXUldXNEdjbXREVW8rSVhZT2t3MWh3UldqdkJtcExHMVZpMFhPckltbmQybTVZdWk1bHo0b1ZlekFRN1NjYVlrdDBoVEdQU1Z2UHpmVlowYWJCQlpiRmViK1hUV2tpSnBPMHBO T3dodGNadHYrN3RMMnc1OFN3QnhVTUk4NzUzdG5Sc1h1blBXZERqcUsxSDA9IGxhcHRldnMtcHV0dHk =
ipaUniqueID:68d46dac-1d3c-11e9-82fd-0242ac110002
krbExtraData:AAL4VkVcbGFwdGV2c0BPTUlLUk9OLlBSTwA =
krbLastFailedAuth:20190123084142Z
krbLastPwdChange:20190121052200Z
krbLoginFailedCount:0
krbPassword到期时间:20190421052200Z
成员:cn = otrs-admins,cn =组,cn =帐户,dc =我的公司,dc = com
成员:cn = ipausers,cn =组,cn =帐户,dc =我的公司,dc = com
mepManagedEntry:cn = laptevs,cn =组,cn =帐户,dc =我的公司,dc = com
objectClass:顶部
objectClass:人
objectClass:组织人员
objectClass:inetorgperson
objectClass:inetuser
objectClass:posixaccount
objectClass:krbprincipalaux
objectClass:krbticketpolicyaux
objectClass:ipaobject
objectClass:ipasshuser
objectClass:ipaSshGroupOfPubKeys
objectClass:mepOriginEntry
dn :uid = laptevs,cn =用户,cn =帐户,dc =我的公司,dc = com
uid :laptevs
名字 :Stanislav
sn :拉普捷夫
cn :拉普捷夫·斯坦尼斯拉夫(Laptev Stanislav)
邮件 :laptevs@MY-IT-COMPANY.COM
l :莫斯科
电话号码 :+7(863)999-99-99
手机 :+7(999)999-99-99
ou :我的公司
标题 :SysAdm
配置OTRS
配置文件
- / opt / otrs / -通常,OTRS系统文件位于此处
- 内核/ Config.pm-您正在编辑的配置文件
- Kernel / Config / Defaults.pm-具有标准设置的文件,您无法对其进行编辑,但可以在其中查看所有现有参数并对其进行注释
代理设定
代理验证
同步代理(具有OTRS角色的LDAP组)
如果您认为角色不适合您,并且只想要组,那么我将举两个将LDAP组与OTRS组同步的示例-简化后的示例,并为每个组设置权限。
备用代理同步(具有OTRS组的LDAP组,具有权限) 替代的简化代理同步(具有OTRS角色且具有rw特权的LDAP组) 客户设置
客户认证
客户端同步(从LDAP获取客户端属性,与OTRS公司进行通信)
结论
如您所见,在OTRS中设置身份验证和帐户同步非常简单,但是我希望本文对那些刚开始熟悉该系统的人有所帮助。
本文剩下什么呢?
- 与LDAP并行运行时,您还可以运行SSO授权,这将使客户端的生活更加轻松。
- 如果您有Perl专家,则可以编写自己的后端以连接到其他信息系统。
- 故意简化了配置,例如,没有属于LDAP组的过滤单元,没有域后缀,BASE DN,使用其他属性,在其他端口上使用LDAP等
在PM中的注释,错别字信息中欢迎提示和澄清。
谢谢您的关注。 特别感谢在多年以前当我被介绍给这个系统时在OTRS上使用的材料:
Turilion ,
supersuperoleg ,
wmlex