安排向订户分配IP地址的任务已经到来。 任务条件:
- 我们不会提供单独的服务器进行授权-您将进行管理;)
- 订户必须通过DHCP接收网络设置
- 网络是多样的。 这是PON设备,是配置了选项82的普通交换机和带点的WiFi基座
- 如果数据不属于发布IP的任何条件,则有必要从“来宾”网络发布IP
从好的方面来看:FreeBSD上有一个服务器可以“工作”,但是“很远”;),它不是“在这个网络上正确的”。
还有一个很棒的Mikrotik设备。 总体网络图如下所示:

经过一番思考,决定使用FreeRadius用户发布网络设置。 原则上,该方案是通常的方案:在Microtick上,我们在同一Radius客户端上打开DHCP服务器。 我们配置了一堆DHCP服务器-> Radius客户端-> Radius服务器。
似乎并不困难。 但是! 细节在于魔鬼。 即:
- 当根据此方案授权PON OLT时,会将请求发送给FreeRadius,其用户名等于头站的MAC地址,Agent-Circuit-Id等于PON Onu MAC,空密码。
- 使用带有选项82的交换机进行授权时,将向FreeRadius发送一个请求,请求中的用户名为空,该用户名等于订户的MAC设备,附加的Agent-Circuit-Id和Agent-Remote-Id附加属性又包含中继交换机MAC和订户连接的端口。
- 一些具有WiFI点的订户是通过PAP-CHAP协议授权的
- 某些具有WIFI点的订户被授权使用与WIFI点的MAC地址相等的用户名,而无需输入密码。
历史背景:什么是DHCP的Option 82
这些是DHCP协议的其他选项,使您可以传输其他信息,例如,在Agent-Circuit-Id和Agent-Remote-Id字段中。 通常用于传输中继交换机的MAC地址和用户连接到的端口。 对于PON设备或WIFI基站,Agent-Circuit-Id字段不携带有用的信息(没有用户端口)。 在这种情况下,DHCP的一般方案如下:
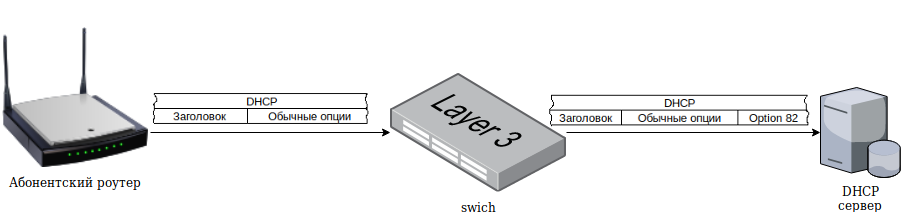
逐步,此方案如下所示:
- 订户设备发出广播DHCP请求以进行网络设置
- 订户设备直接连接到的设备(例如,交换机,WiFi或PON基站)“截获”该数据包并对其进行修改,将其他选项Option 82和中继代理IP地址引入其中,然后通过网络进一步传输。
- DHCP服务器接受请求,形成响应并将其发送到中继设备
- 中继设备将响应分组转发到订户设备
因此,所有这些都不起作用,当然,您需要对网络设备进行适当的配置。
安装FreeRadius
当然,有了FreeRadius配置设置,您就可以实现所有这些功能,但是这很困难而且不清楚……尤其是当您在N个月“一切正常”之后窥探那里时。 因此,决定用Python编写FreeRadius的授权模块。 我们将从MySQL数据库获取数据以进行授权。 描述它的结构是没有意义的,无论如何,每个人都将“自己做”。 特别是,我采用了FreeRadius的sql模块所建议的结构,并通过添加了每个用户的mac和port字段以及登录密码对它进行了少许更改。
因此,对于初学者,请安装FreeRadius:
cd /usr/ports/net/freeradius3 make config make install clean
在设置中,我们标记为安装:
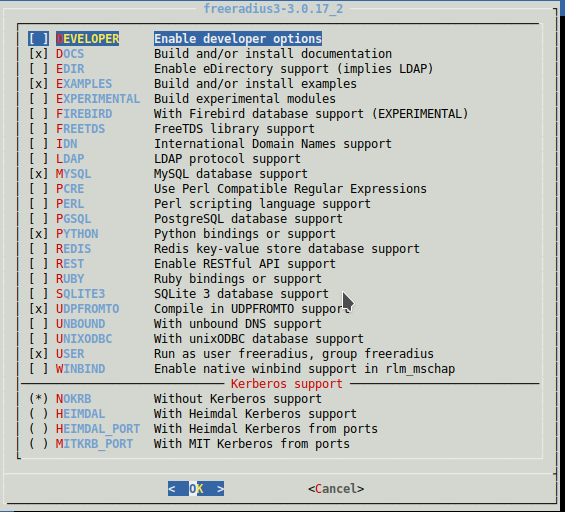
我们建立到python模块的符号链接(即,将其打开):
ln -s /usr/local/etc/raddb/mods-available/python /usr/local/etc/raddb/mods-enabled
为python安装一个附加模块:
pip install mysql-connector
在FreeRadius的python模块设置中,您需要在python_path变量中指定模块搜索路径。 例如,我有这个:
python_path="/usr/local/etc/raddb/mods-config/python:/usr/local/lib/python2.7:/usr/local/lib/python27.zip:/usr/local/lib/python2.7:/usr/local/lib/python2.7/plat-freebsd12:/usr/local/lib/python2.7/lib-tk:/usr/local/lib/python2.7/lib-old:/usr/local/lib/python2.7/lib-dynload:/usr/local/lib/python2.7/site-packages"
可以通过运行python解释器并输入以下命令来找到路径:
root@phaeton:/usr/local/etc/raddb/mods-enabled
如果您不执行此步骤,则用python编写并由FreeRadius运行的脚本将找不到在import中列出的模块。 另外,有必要在模块设置中取消对授权和计费功能的注释。 例如,此模块如下所示:
python { python_path="/usr/local/etc/raddb/mods-config/python:/usr/local/lib/python2.7:/usr/local/lib/python2.7/site-packages:/usr/local/lib/python27.zip:/usr/local/lib/python2.7:/usr/local/lib/python2.7/plat-freebsd12:/usr/local/lib/python2.7/lib-tk:/usr/local/lib/python2.7/lib-old:/usr/local/lib/python2.7/lib-dynload:/usr/local/lib/python2.7/site-packages" module = work mod_instantiate = ${.module} mod_detach = ${.module} mod_authorize = ${.module} func_authorize = authorize mod_authenticate = ${.module} func_authenticate = authenticate mod_preacct = ${.module} func_preacct = preacct mod_accounting = ${.module} func_accounting = accounting mod_checksimul = ${.module} mod_pre_proxy = ${.module} mod_post_proxy = ${.module} mod_post_auth = ${.module} mod_recv_coa = ${.module} mod_send_coa = ${.module} }
必须将work.py脚本(以及其他所有人)放在/ usr / local / etc / raddb / mods-config / python中。共有三个脚本。
从代码中可以看到,我们正在通过所有可用的方法尝试通过其明显已知的订户MAC地址或Option 82捆绑包来识别订户,如果仍无法解决,我们将发布“来宾”网络中使用的最早的IP地址。 仍然需要在启用了sites的文件夹中配置默认脚本,以便python脚本在必要的时间抽动必要的功能。 实际上,将文件带到表单就足够了:
默认值 server default { listen { type = auth ipaddr = * port = 0 limit { max_connections = 16 lifetime = 0 idle_timeout = 30 } } listen { ipaddr = * port = 0 type = acct limit { } } listen { type = auth port = 0 limit { max_connections = 1600 lifetime = 0 idle_timeout = 30 } } listen { ipv6addr = :: port = 0 type = acct limit { } } authorize { python filter_username preprocess expiration logintime } authenticate { Auth-Type PAP { pap python } Auth-Type CHAP { chap python } Auth-Type MS-CHAP { mschap python } eap } preacct { preprocess acct_unique suffix files } accounting { python exec attr_filter.accounting_response } session { } post-auth { update { &reply: += &session-state: } exec remove_reply_message_if_eap Post-Auth-Type REJECT { attr_filter.access_reject eap remove_reply_message_if_eap } Post-Auth-Type Challenge { } } pre-proxy { } post-proxy { eap } }
我们尝试运行并查看运行调试日志的方式:
/usr/local/etc/rc.d/radiusd debug
还有什么 设置FreeRadius时,可以使用radclient实用程序方便地测试其操作。 例如授权:
echo "User-Name=4C:5E:0C:2E:7F:15,Agent-Remote-Id=0x9845623a8c98,Agent-Circuit-Id=0x00010006" | radclient -x 127.0.0.1:1812 auth testing123
或会计:
echo "User-Name=4C:5E:0C:2E:7F:15,Agent-Remote-Id=0x00030f26054a,Agent-Circuit-Id=0x00010002" | radclient -x 127.0.0.1:1813 acct testing123
我要警告的是,不可能以“工业”规模使用类似的方案和“无变化”的脚本。 至少引人注目:
- 可能的“假” MAC地址。 订户为自己注册一个外部MAC足够了,并且会出现问题
- 发出来宾网络的逻辑首先受到批评。 甚至没有支票“您已经有这样的IP地址的客户端了吗?”
为了在我的条件下专门工作,这仅仅是“膝上的解决方案”,仅此而已。 不要严格判断;)