-0x01-简介
本文致力于分析Flare-On 2019的所有任务-FlaE-On年度逆向工程竞赛。 在这些比赛中,我第二次参加了比赛。 在前一年,我在大约13天内解决了所有问题,在完成时间方面排名达到第11位。 今年,这组任务比较容易,我花了54个小时见了面,同时在交付方面名列第三。
在本文中,我试图描述那些引起我最大兴趣的时刻,因此,该分析将不会描述在IDA中工作的例程,了解每个功能的算法以及其他不太有趣的地方。 我希望阅读此书后,您会发现一些对自己有用的新东西。 您可以从作者那里找到问题的分析,以及一些获奖者的统计数据和奖品。
如果您有兴趣,那就欢迎猫!
0x00-内容
- 0x01-Memecat Battlestation [共享软件演示版]
- 0x02-超长
- 0x03-Flarebear
- 0x04-Dnschess
- 0x05-演示
- 0x06-bmphide
- 0x07-wopr
- 0x08-蛇
- 0x09-重新加载
- 0x0A-Mugatu
- 0x0B-vv_max
- 0x0C-帮助
- 0x0D-摘要
0x01-Memecat Battlestation [共享软件演示版]
欢迎参加第六届Flare-On挑战赛!
这是一个简单的游戏。 对其进行反向工程以弄清楚要击败两个敌人所需要输入的“武器代码”,并且胜利屏幕会显示该标志。 在此站点上的此处输入标志以得分并前进到下一个级别。
*此挑战是用.NET编写的。 如果您还没有最喜欢的.NET逆向工程工具,我建议dnSpy
**如果您已经在BlackHat的展位上解决了该游戏的完整版本,或者随后在Twitter上发布了此版本,那么祝贺您,请立即从胜利屏幕输入标志,以绕过此级别。
这项任务是我在确定Black Hat USA 2019的一部分时预先安排的。 我不记得他是怎么解决的 任务非常简单,因此我们将不考虑其解决方案。
0x02-超长
巧妙地隐藏了下一个挑战的秘密。 但是,采用正确的方法,找到解决方案不会花费很长时间。
给定x86 .exe文件。 当您尝试启动时,将显示一条消息,其中包含以下内容:
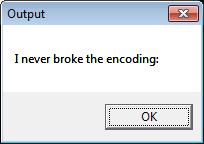
分析应用程序时,您可能会发现消息以某种字符长度(从1到4字节)可变的编码存储。 调用解码功能时,它接收到预期结果的长度,该长度比消息本身短,这就是为什么该标志不可见的原因。 您可以固定在调试模式下传递给函数的长度值,并获得带有标志的完整消息:

您还可以用Python重写解码算法并获得一个标志:
msg = [ ... ]
0x03-Flarebear
Flare的我们创建了自己的Tamagotchi宠物flarebear。 他很挑剔。 让他活着快乐,他会给你旗子。
在此任务中, Android了Android的apk文件。 考虑一种不启动应用程序本身的解决方案方法。
第一步是获取应用程序的源代码。 为此,请使用dex2jar实用程序dex2jar将apk转换为jar ,然后使用反编译器获取Java源代码,我更喜欢将cfr 。
~/retools/d2j/d2j-dex2jar.sh flarebear.apk java -jar ~/retools/cfr/cfr-0.146.jar --outputdir src flarebear-dex2jar.jar
通过分析应用程序的源代码,您可以找到一个有趣的.danceWithFlag()方法,该方法位于FlareBearActivity.java文件中。 在.danceWithFlag()内部,使用.decrypt(String, byte[])方法解密raw应用程序资源,该方法的第一个参数是使用.getPassword()方法获得的字符串。 该标志肯定在加密的资源中,因此让我们尝试对其进行解密。 为此,我决定稍微重写一下反编译的代码,摆脱了Android依赖,只保留了解密所需的方法,以便可以对生成的代码进行编译。 此外,在分析过程中,发现.getPassword()方法取决于三个整数状态值。 每个值的范围都介于0到N ,因此您可以浏览所有可能的值以查找所需的密码。
结果是以下代码:
Main.java import java.io.InputStream; import java.nio.charset.Charset; import java.security.Key; import java.security.spec.AlgorithmParameterSpec; import java.security.spec.KeySpec; import java.util.ArrayList; import java.util.Collection; import java.util.HashMap; import java.util.List; import java.util.stream.Collectors; import java.util.Collections; import java.io.*; import javax.crypto.Cipher; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.IvParameterSpec; import javax.crypto.spec.PBEKeySpec; import javax.crypto.spec.SecretKeySpec; public final class Main { public static void main (String args []) throws Exception { Main a = new Main(); InputStream inputStream = new FileInputStream("ecstatic"); long fileSize = new File("ecstatic").length(); byte[] file1 = new byte[(int) fileSize]; inputStream.read(file1); inputStream = new FileInputStream("ecstatic2"); fileSize = new File("ecstatic2").length(); byte[] file2 = new byte[(int) fileSize]; inputStream.read(file2); for(int i = 0; i < 9; i++) { for(int j = 0; j < 7; j++) { for(int k = 1; k < 16; k++) { String pass = a.getPassword(i, j, k); try { byte[] out1 = a.decrypt(pass, file1); byte[] out2 = a.decrypt(pass, file2); OutputStream outputStream = new FileOutputStream("out1"); outputStream.write(out1); outputStream = new FileOutputStream("out2"); outputStream.write(out2); System.out.println("yep!"); } catch (javax.crypto.BadPaddingException ex) { } } } } } public final byte[] decrypt(Object object, byte[] arrby) throws Exception { Object object2 = Charset.forName("UTF-8"); object2 = "pawsitive_vibes!".getBytes((Charset)object2); object2 = new IvParameterSpec((byte[])object2); object = ((String)object).toCharArray(); Object object3 = Charset.forName("UTF-8"); object3 = "NaClNaClNaCl".getBytes((Charset)object3); object = new PBEKeySpec((char[])object, (byte[])object3, 1234, 256); object = SecretKeyFactory.getInstance("PBKDF2WithHmacSHA1").generateSecret((KeySpec)object); object3 = new SecretKeySpec(((SecretKey)object).getEncoded(), "AES"); object = Cipher.getInstance("AES/CBC/PKCS5Padding"); ((Cipher)object).init(2, (Key)object3, (AlgorithmParameterSpec)object2); object = ((Cipher)object).doFinal(arrby); return (byte [])object; } public final String getPassword(int n, int n2, int n3) { String string2 = "*"; String string3 = "*"; switch (n % 9) { case 8: { string2 = "*"; break; } case 7: { string2 = "&"; break; } case 6: { string2 = "@"; break; } case 5: { string2 = "#"; break; } case 4: { string2 = "!"; break; } case 3: { string2 = "+"; break; } case 2: { string2 = "$"; break; } case 1: { string2 = "-"; break; } case 0: { string2 = "_"; } } switch (n3 % 7) { case 6: { string3 = "@"; break; } case 4: { string3 = "&"; break; } case 3: { string3 = "#"; break; } case 2: { string3 = "+"; break; } case 1: { string3 = "_"; break; } case 0: { string3 = "$"; } case 5: } String string4 = String.join("", Collections.nCopies(n / n3, "flare")); String string5 = String.join("", Collections.nCopies(n2 * 2, this.rotN("bear", n * n2))); String string6 = String.join("", Collections.nCopies(n3, "yeah")); StringBuilder stringBuilder = new StringBuilder(); stringBuilder.append(string4); stringBuilder.append(string2); stringBuilder.append(string5); stringBuilder.append(string3); stringBuilder.append(string6); return stringBuilder.toString(); } public final String rotN(String charSequence, int n) { Collection<String> collection = new ArrayList(charSequence.length()); for (int i = 0; i < charSequence.length(); ++i) { char c; char c2 = c = charSequence.charAt(i); if (Character.isLowerCase(c)) { char c3; c2 = c3 = (char)(c + n); if (c3 > 'z') { c2 = c3 = (char)(c3 - n * 2); } } collection.add(Character.valueOf(c2).toString()); } return collection.stream().collect(Collectors.joining());
我们将提取加密的资源,编译并运行结果文件:
$ ~/retools/apktool/apktool d flarebear.apk $ cp flarebear/res/raw/* . $ javac Main.java $ java Main
幸运的是,您选择的所有密码选项中只有一个适合。 结果,我们得到两个带有标志的图像:
~/flareon2019/3 - Flarebear$ file out* out1: PNG image data, 2100 x 2310, 8-bit/color RGB, non-interlaced out2: PNG image data, 2100 x 2310, 8-bit/color RGB, non-interlaced


0x04-Dnschess
一些可疑的网络流量将我们引向运行在Ubuntu桌面上的未经授权的国际象棋程序。 这似乎是网络空间计算机黑客的工作。 您需要采取正确的措施来解决这一问题。 祝你好运!
该任务包含一个流量转储,一个ELF可执行文件ChessUI和一个库ChessAI.so 。 通过运行可执行文件,您可以看到棋盘。
让我们从流量转储开始分析。

所有流量都包含对A DNS服务器的查询。 查询本身包括棋子的名称,下棋游戏的动作的描述以及.game-of-thrones.flare-on.com的恒定部分,例如rook-c3-c6.game-of-thrones.flare-on.com 。 通过不断的工作,您可以轻松地在ChessAI.so库中找到合适的位置:
signed __int64 __fastcall getNextMove(int idx, const char *chess_name, unsigned int pos_from, unsigned int pos_to, \__int64 a5) { struct hostent *v9;
从代码中可以看出,基于接收到的ip地址,解密了某个字节字符串,该字节字符串存储在另一个存储区中,我称之为flag 。
要解决此任务,首先要做的是从流量转储中获取所有ip地址。 您可以使用以下命令执行此操作:
tshark -r capture.pcap | grep -P -o '127.(\d+).(\d+).(\d+)' | grep -v '127.0.0.1'
将所有ip地址保存到ips文件后,可以使用以下Python代码获取该标志:
with open('ips') as f: ips = f.read().split() flag = bytearray(64) key = b'yZ\xb8\xbc\xec\xd3\xdf\xdd\x99\xa5\xb6\xac\x156\x85\x8d\t\x08wRMqT}\xa7\xa7\x08\x16\xfd\xd7' for ip in ips: a, b, c, d = map(int, ip.split('.')) if d & 1: continue idx = c & 0xf if idx > 14: continue flag[2*idx] = b ^ key[2*idx] flag[2*idx + 1] = b ^ key[2*idx + 1] print(flag.decode() + '@flare-on.com')
0x05-演示
Flare团队中的某人试图以其过人的技巧打动我们。 似乎是空白。 看看您是否能解决问题,否则我们将不得不解雇他们。 没有压力
给定可执行文件4k.exe ,该文件使用DirectX 。 启动后,旋转的FlareOn徽标显示在主窗口中。

程序的静态分析揭示了一个功能,它是切入点。 在内容上,该功能类似于代码解密的实现。 我们不会浪费时间分析此函数的算法,只需在ret指令上放置一个断点,然后查看将控件转移到哪里。 返回后,我们发现0x00420000位于地址0x00420000 ,该代码在此处被反汇编为足够的东西:
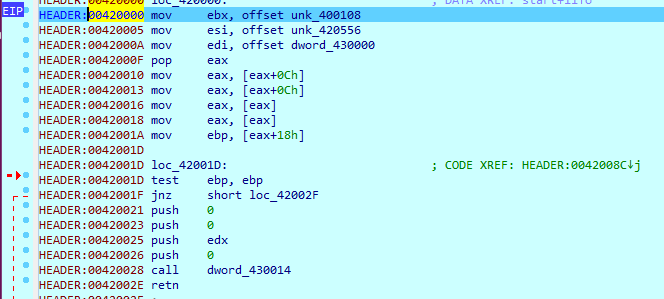
然后决定使用API将代码从调试模式转移到IDA数据库,并继续进行静态分析。
开头的新代码从各种库中导入了必要的功能。 这些功能表也可以动态恢复。 结果是以下功能集:
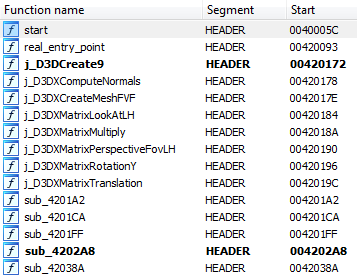
该程序的“真实”入口点将是:

请注意DeviceInterface类型为IDirect3DDevice9 **的DeviceInterface的创建。 将来,将积极使用此接口,并且为了简化反向操作,有必要定义其方法表。 例如,可以在此处快速找到接口的定义。 我解析了该表并将其转换为IDA的结构。 将结果类型应用于DeviceInterface可以大大简化进一步的代码分析。 以下屏幕快照显示了应用该类型前后场景渲染周期主要功能的反编译器结果。
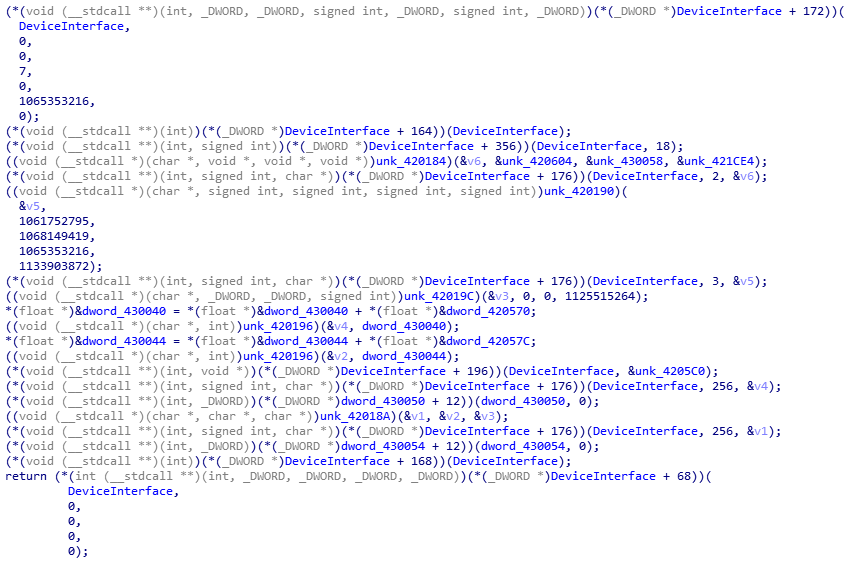

经过进一步分析,发现在程序中创建了两个多边形网格(网格,多边形网格),尽管在程序运行时我们仅看到一个对象。 同样,在构建网格时,其顶点使用XOR加密,这也引起了怀疑。 让我们解密并可视化顶点。 第二个网格最受关注,因为 它具有更多的顶点。 matplotlib所有顶点后,我发现每个顶点的Z坐标均为0,因此为了可视化,决定使用matplotlib绘制二维图形。 以下代码和结果带有标志:
import struct import matplotlib.pyplot as plt with open('vertexes', 'rb') as f: data = f.read() n = len(data) // 4 data = list(struct.unpack('{}I'.format(n), data)) key = [0xCB343C8, 0x867B81F0, 0x84AF72C3] data = [data[i] ^ key[i % 3] for i in range(len(data))] data = struct.pack('{}I'.format(n), *data) data = list(struct.unpack('{}f'.format(n), data)) x = data[0::3] y = data[1::3] z = data[2::3] print(z) plt.plot(x, y) plt.show()

0x06-bmphide
泰勒·迪恩(Tyler Dean)爬了山。 Elbert(科罗拉多州的最高山峰)在凌晨2点捕捉到这张照片的最佳时间。 千万不要跳过腿部运动。 我们发现了这张图片,并且可以在他留在小径顶部的拇指驱动器上执行。 他可以信任吗?
在任务中,给出了可执行文件bmphide.exe和image.bmp image。 可以假设使用隐写术方法在图像中隐藏了某些消息。
二进制文件是用C#编写的,因此我使用dnSpy实用程序进行了分析。 您会立即注意到,大多数方法名称都被混淆了。 如果查看Program.Main方法,则可以了解程序的逻辑并对其某些用途进行假设:
- 使用
Program.Init()方法初始化应用程序 - 读取数据文件和图像文件
- 使用
byte [] Program.h(byte [])方法,执行一些数据转换 - 使用
Program.i(Bitmap, byte[])方法Program.i(Bitmap, byte[]) ,将转换后的数据插入到图像中 - 结果图像将以新名称保存。
初始化应用程序时, A调用A类A各种方法。 对该类进行的表面分析表明,该类的某些方法与混淆器ConfuserEx (文件AntiTamper.JIT.cs )的方法相似。 该应用程序确实受到了调试保护。 同时,无法使用de4dot实用程序及其前叉删除保护机制,因此决定继续进行分析。
考虑Program.i方法,该方法用于将数据插入图像。
public static void i(Bitmap bm, byte[] data) { int num = Program.j(103); for (int i = Program.j(103); i < bm.Width; i++) { for (int j = Program.j(103); j < bm.Height; j++) { bool flag = num > data.Length - Program.j(231); if (flag) { break; } Color pixel = bm.GetPixel(i, j); int red = ((int)pixel.R & Program.j(27)) | ((int)data[num] & Program.j(228)); int green = ((int)pixel.G & Program.j(27)) | (data[num] >> Program.j(230) & Program.j(228)); int blue = ((int)pixel.B & Program.j(25)) | (data[num] >> Program.j(100) & Program.j(230)); Color color = Color.FromArgb(Program.j(103), red, green, blue); bm.SetPixel(i, j, color); num += Program.j(231); } } }
但是,与经典LSB非常相似,在需要常量的地方,使用int Program.j(byte)方法。 它的工作结果取决于所获得的各种全局值,包括在Program.Init()方法中进行初始化期间。 决定不撤消他的工作,而是在运行时获取所有可能的值。 dnSpy允许dnSpy编辑反编译的应用程序代码并保存修改后的模块。 我们利用这一点并重写Program.Main方法,如下所示:
private static void Main(string[] args) { Program.Init(); Program.yy += 18; for (int i = 0; i < 256; i++) { Console.WriteLine(string.Format("j({0}) = {1}", i, Program.j((byte)i))); } }
在启动时,我们获得以下值:
E:\>bmphide_j.exe j(0) = 206 j(1) = 204 j(2) = 202 j(3) = 200 j(4) = 198 j(5) = 196 j(6) = 194 j(7) = 192 j(8) = 222 j(9) = 220 j(10) = 218 j(11) = 216 j(12) = 214 j(13) = 212 j(14) = 210 j(15) = 208 j(16) = 238 j(17) = 236 j(18) = 234 j(19) = 232 j(20) = 230 ...
用结果常量替换对Program.j方法中对Program.j的调用:
public static void i(Bitmap bm, byte[] data) { int num = 0; for (int i = 0; i < bm.Width; i++) { for (int j = 0; j < bm.Height; j++) { bool flag = num > data.Length - 1; if (flag) { break; } Color pixel = bm.GetPixel(i, j); int red = ((int)pixel.R & 0xf8) | ((int)data[num] & 0x7); int green = ((int)pixel.G & 0xf8) | (data[num] >> 3 & 0x7); int blue = ((int)pixel.B & 0xfc) | (data[num] >> 6 & 0x3); Color color = Color.FromArgb(0, red, green, blue); bm.SetPixel(i, j, color); num += 1; } } }
现在很清楚如何将消息的每个字节插入图像中:
- 位0到2放置在该点的红色通道的3个LSB中
- 第3至5位位于该点的绿色通道的3个LSB中
- 第6至7位位于该点的蓝色通道的2个LSB中
接下来,我尝试重复数据转换方法的算法,但是计算结果与程序的输出不匹配。 事实证明,类A还具有替换方法(在A.VerifySignature(MethodInfo m1, MethodInfo m2) )和修改方法字节码的IL (在A.IncrementMaxStack )的功能。
要在Program的Program.Init选择需要替换的方法,将对这些方法的字节码IL哈希处理并与预先计算的值进行比较。 总共替换了两种方法。 为了找出哪个,我们将通过在A.VerifySignature调用上设置断点来在调试器下启动应用程序,并且您必须跳过Program.Init的调用A.CalculateStack() ,因为 它防止调试。

结果,您可以看到Program.a方法被Program.b替换,而Program.c被Program.c替换。
现在,您需要处理字节码的修改:
private unsafe static uint IncrementMaxStack(IntPtr self, A.ICorJitInfo* comp, A.CORINFO_METHOD_INFO* info, uint flags, byte** nativeEntry, uint* nativeSizeOfCode) { bool flag = info != null; if (flag) { MethodBase methodBase = Ac(info->ftn); bool flag2 = methodBase != null; if (flag2) { bool flag3 = methodBase.MetadataToken == 100663317; if (flag3) { uint flNewProtect; A.VirtualProtect((IntPtr)((void*)info->ILCode), info->ILCodeSize, 4u, out flNewProtect); Marshal.WriteByte((IntPtr)((void*)info->ILCode), 23, 20); Marshal.WriteByte((IntPtr)((void*)info->ILCode), 62, 20); A.VirtualProtect((IntPtr)((void*)info->ILCode), info->ILCodeSize, flNewProtect, out flNewProtect); } else { bool flag4 = methodBase.MetadataToken == 100663316; if (flag4) { uint flNewProtect2; A.VirtualProtect((IntPtr)((void*)info->ILCode), info->ILCodeSize, 4u, out flNewProtect2); Marshal.WriteInt32((IntPtr)((void*)info->ILCode), 6, 309030853); Marshal.WriteInt32((IntPtr)((void*)info->ILCode), 18, 209897853); A.VirtualProtect((IntPtr)((void*)info->ILCode), info->ILCodeSize, flNewProtect2, out flNewProtect2); } } } } return A.originalDelegate(self, comp, info, flags, nativeEntry, nativeSizeOfCode); }
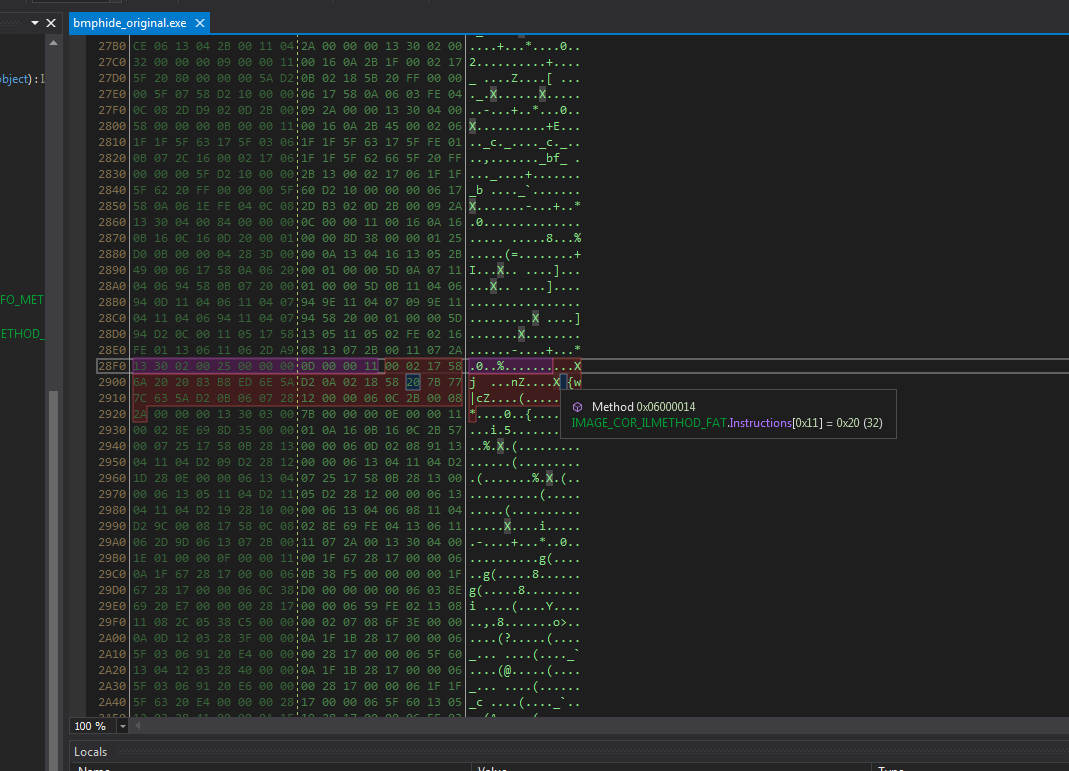
显然,具有特定MetadataToken值(即0x6000015和0x6000014 )的方法将被修改。 这些标记对应于Program.h和Program.g方法。 dnSpy有一个内置的hex编辑器,当悬停时,其中的方法数据将突出显示:其标题(以紫色突出显示)和字节码(以红色突出显示),如屏幕截图所示。 您可以在hex编辑器中通过在反编译方法之前单击注释中的相应地址来转到所需的方法(例如, File Offset: 0x00002924 )。
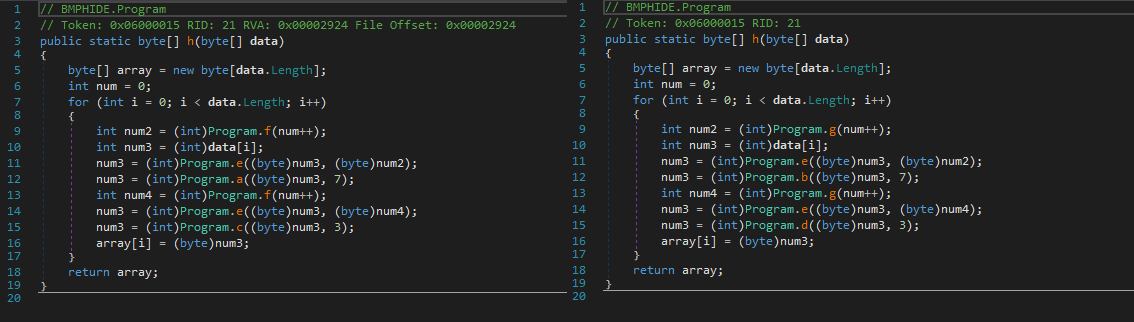
让我们尝试应用所有描述的修改:我们将创建文件的副本,在任何十六进制编辑器中,我们将在必要的偏移量处更改值,这是从dnSpy中学到的dnSpy并将替换Program.h dnSpy a -> b和c -> d方法。 我们还将从Program.Init删除对模块A所有调用A 如果一切都正确完成,那么当我们尝试使用修改后的应用程序将某些消息插入图片时,我们将获得与原始应用程序正常工作时相同的结果。 下面的屏幕快照显示了原始和修改后的应用程序方法的反编译代码。
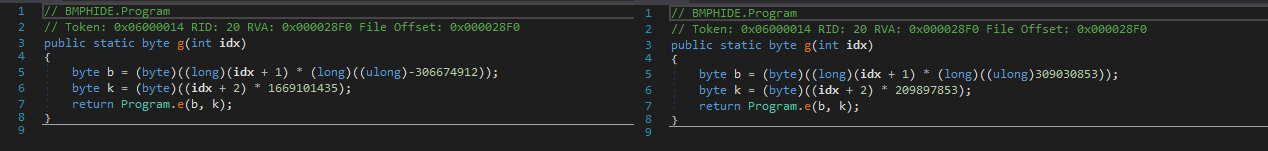
剩下的是创建逆变换算法。 这很简单,因此我只给出生成的Python脚本:
from PIL import Image
通过运行此脚本,我们将获得另一个没有标志的bmp图像。 在上面重复该过程,我们得到带有标志的最终图像。

0x07-wopr
我们使用自己的计算机黑客技能在军事超级计算机上“找到”该AI。 它确实很像1983年的经典电影《战争游戏》。 也许生活模仿艺术? 如果您可以找到我们的启动代码,我们将让您继续进行下一个挑战。 我们保证不会发动热核战争。
在任务中,将worp.exe控制台应用程序worp.exe 。 显然,要解决此问题,您需要选择一些代码。
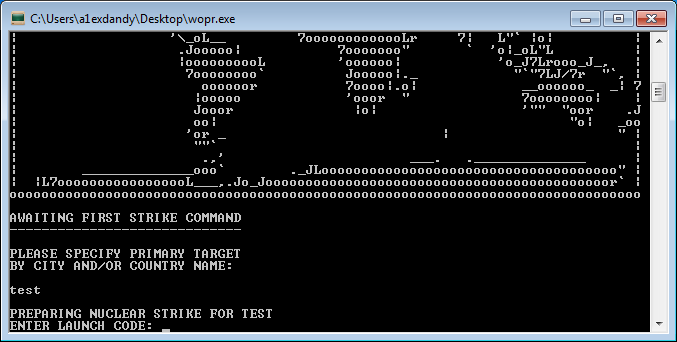
对入口点的分析表明,这是一个自解压的存档。 启动时, _MEIPASS2环境变量_MEIPASS2 。 如果此变量不存在,则会创建一个临时目录,将存档的内容解压缩到该目录中,然后应用程序将使用给定的环境变量_MEIPASS2 。 存档内容:
. ├── api-ms-win-core-console-l1-1-0.dll ├── ... ├── ... ├── api-ms-win-crt-utility-l1-1-0.dll ├── base_library.zip ├── _bz2.pyd ├── _ctypes.pyd ├── _hashlib.pyd ├── libcrypto-1_1.dll ├── libssl-1_1.dll ├── _lzma.pyd ├── pyexpat.pyd ├── python37.dll ├── select.pyd ├── _socket.pyd ├── _ssl.pyd ├── this │ ├── __init__.py │ └── key ├── ucrtbase.dll ├── unicodedata.pyd ├── VCRUNTIME140.dll └── wopr.exe.manifest 1 directory, 56 files
从内容来看,我们正在处理exe打包的Python应用程序。 为此,您可以在主二进制文件中找到Python库相应功能的动态导入: PyMarshal_ReadObjectFromString , PyEval_EvalCode等。 为了进一步分析,您需要提取Python字节码。 为此,请从临时目录中保存归档文件的内容,并将_MEIPASS2路径_MEIPASS2环境变量_MEIPASS2 。 通过在PyMarshal_ReadObjectFromString函数上设置断点,以调试模式运行主二进制文件。 此函数将指向带有序列化Python代码及其长度的缓冲区的指针作为参数。 我们为每个调用转储已知长度的缓冲区的内容。 我只有2个调用,而在第二个中,序列化的对象要大得多,我们将对其进行分析。
分析获得的数据的一种相当简单的方法是将其转换为.pyc文件(已编译的Python字节码)的格式,并使用uncompyle6反编译。 为此,只需在接收到的数据中添加一个16字节的标头即可。 结果,我得到以下文件:
00000000: 42 0d 0d 0a 00 00 00 00 de cd 57 5d 00 00 00 00 B.........W].... 00000010: e3 00 00 00 00 00 00 00 00 00 00 00 00 09 00 00 ................ 00000020: 00 40 00 00 00 73 3c 01 00 00 64 00 5a 00 64 01 .@...s<...dZd 00000030: 64 02 6c 01 5a 01 64 01 64 02 6c 02 5a 02 64 01 dlZddlZd
接下来,我们使用uncompyle6反编译结果文件:
uncompyle6 task.pyc > task.py
如果尝试运行反编译的文件,则在BOUNCE = pkgutil.get_data('this', 'key')行中将出现异常。 只需将存档中的key文件内容分配给BOUNCE变量,即可轻松解决此问题。 重新运行脚本,我们只会看到铭文LOADING... 显然,该任务中使用了一些防止反编译的技术。 我们继续分析生成的Python代码。 最后,我们看到以下循环:
for i in range(256): try: print(lzma.decompress(fire(eye(__doc__.encode()), bytes([i]) + BOUNCE))) except Exception: pass
您可以理解, print函数实际上是作为exec覆盖的,其参数仅取决于__doc__.encode() -文件开头的文本。在代码执行开始时,将函数保存print为其他名称,然后将其替换print在块中try-except。当我们运行生成的脚本时,将不会再显示任何内容。也许反编译__doc__记录不正确。让我们尝试__doc__直接从序列化代码中提取值,如下所示:
import marshal with open('pycode1', 'rb') as inp: data = inp.read() code = marshal.loads(data) doc = code.co_consts[0] with open('doc.txt', 'w') as outp: outp.write(doc)
再次运行脚本,替换其中的内容__doc__。结果,i代码以某个值成功地显示在屏幕上。我们将其保存在新文件中并进行分析。在函数中,wrong您可以找到以下行:
trust = windll.kernel32.GetModuleHandleW(None)
, . 0x100000 wrong , . , .
. z3 :
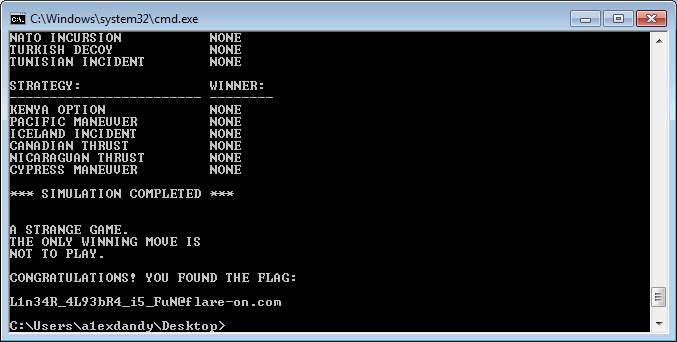
from z3 import * from stage2 import wrong xor = [212, 162, 242, 218, 101, 109, 50, 31, 125, 112, 249, 83, 55, 187, 131, 206] h = list(wrong()) h = [h[i] ^ xor[i] for i in range(16)] b = 16 * [None] x = [] for i in range(16): x.append(BitVec('x' + str(i), 32)) b[0] = x[2] ^ x[3] ^ x[4] ^ x[8] ^ x[11] ^ x[14] b[1] = x[0] ^ x[1] ^ x[8] ^ x[11] ^ x[13] ^ x[14] b[2] = x[0] ^ x[1] ^ x[2] ^ x[4] ^ x[5] ^ x[8] ^ x[9] ^ x[10] ^ x[13] ^ x[14] ^ x[15] b[3] = x[5] ^ x[6] ^ x[8] ^ x[9] ^ x[10] ^ x[12] ^ x[15] b[4] = x[1] ^ x[6] ^ x[7] ^ x[8] ^ x[12] ^ x[13] ^ x[14] ^ x[15] b[5] = x[0] ^ x[4] ^ x[7] ^ x[8] ^ x[9] ^ x[10] ^ x[12] ^ x[13] ^ x[14] ^ x[15] b[6] = x[1] ^ x[3] ^ x[7] ^ x[9] ^ x[10] ^ x[11] ^ x[12] ^ x[13] ^ x[15] b[7] = x[0] ^ x[1] ^ x[2] ^ x[3] ^ x[4] ^ x[8] ^ x[10] ^ x[11] ^ x[14] b[8] = x[1] ^ x[2] ^ x[3] ^ x[5] ^ x[9] ^ x[10] ^ x[11] ^ x[12] b[9] = x[6] ^ x[7] ^ x[8] ^ x[10] ^ x[11] ^ x[12] ^ x[15] b[10] = x[0] ^ x[3] ^ x[4] ^ x[7] ^ x[8] ^ x[10] ^ x[11] ^ x[12] ^ x[13] ^ x[14] ^ x[15] b[11] = x[0] ^ x[2] ^ x[4] ^ x[6] ^ x[13] b[12] = x[0] ^ x[3] ^ x[6] ^ x[7] ^ x[10] ^ x[12] ^ x[15] b[13] = x[2] ^ x[3] ^ x[4] ^ x[5] ^ x[6] ^ x[7] ^ x[11] ^ x[12] ^ x[13] ^ x[14] b[14] = x[1] ^ x[2] ^ x[3] ^ x[5] ^ x[7] ^ x[11] ^ x[13] ^ x[14] ^ x[15] b[15] = x[1] ^ x[3] ^ x[5] ^ x[9] ^ x[10] ^ x[11] ^ x[13] ^ x[15] solver = Solver() for i in range(16): solver.add(x[i] < 128) for i in range(16): solver.add(b[i] == h[i]) if solver.check() == sat: m = solver.model() print(bytes([m[i].as_long() for i in x])) else: print('unsat')
, : 5C0G7TY2LWI2YXMB
0x08 — snake
The Flare team is attempting to pivot to full-time twitch streaming video games instead of reverse engineering computer software all day. We wrote our own classic NES game to stream content that nobody else has seen and watch those subscribers flow in. It turned out to be too hard for us to beat so we gave up. See if you can beat it and capture the internet points that we failed to collect.
NES - . FCEUX , .. . , .
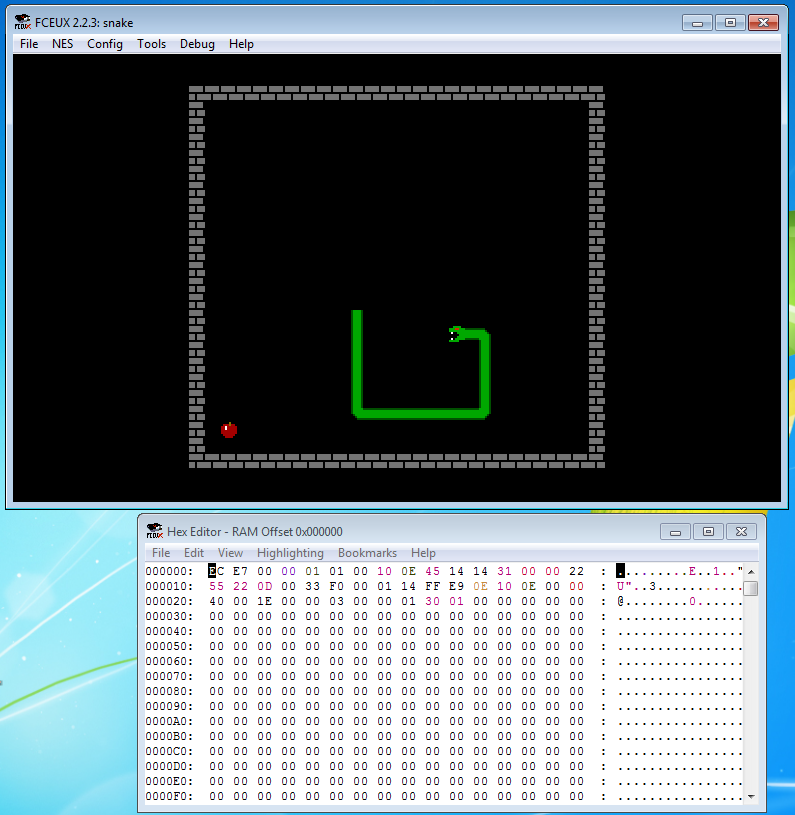
, , 0x25 . , . NES - IDA . inesldr . 0x25 . C82A , . 0x33 .

, — 0x32 0x25 . , . , FCEUX . .
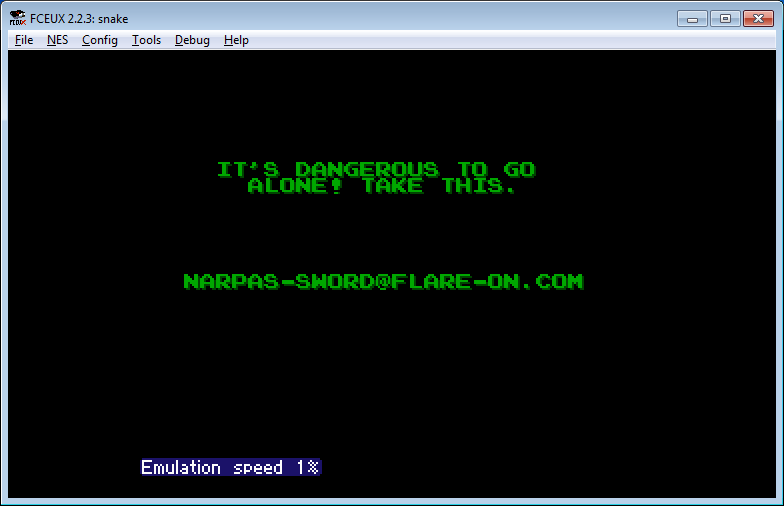
0x09 — reloadered
This is a simple challenge, enter the password, receive the key. I hear that it caused problems when trying to analyze it with ghidra. Remember that valid flare-on flags will always end with @flare-on.com
reloaderd.exe , . , , . , , XOR , @FLAG.com , .
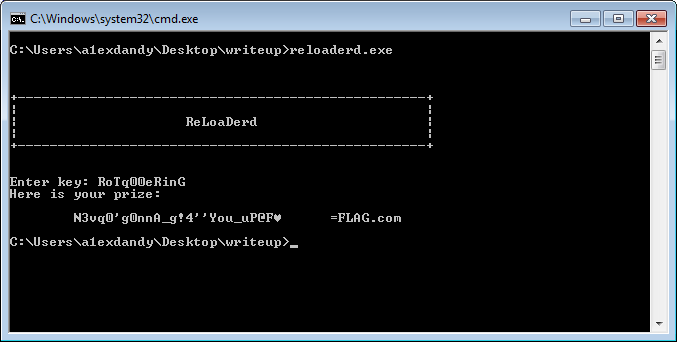
, NOP . , , . . , . , , . , , NOP , .
, , XOR , . @flare-on.com , . :
flag = bytearray(b'D)6\n)\x0f\x05\x1be&\x10\x04+h0/\x003/\x05\x1a\x1f\x0f8\x02\x18B\x023\x1a(\x04*G?\x04&dfM\x107>(>w\x1c?~64*\x00') for i in range(0x539): for j in range(0x34): if (i % 3) == 0 or (i % 7) == 0: flag[j] ^= (i & 0xff) end = b'@flare-on.com' def xor(a, b): return bytes([i^j for i, j in zip(a, b)]) for i in range(len(flag)): print(i, xor(end, flag[i:])) print(xor(flag, b'3HeadedMonkey'*4))
0x0A — Mugatu
Hello,
I'm working an incident response case for Derek Zoolander. He clicked a link and was infected with MugatuWare! As a result, his new headshot compilation GIF was encrypted.
To secure an upcoming runway show, Derek needs this GIF decrypted; however, he refuses to pay the ransom.
We received an additional encrypted GIF from an anonymous informant. The informant told us the GIF should help in our decryption efforts, but we were unable to figure it out.
We're reaching out to you, our best malware analyst, in hopes that you can reverse engineer this malware and decrypt Derek's GIF.
I've included a directory full of files containing:
- MugatuWare malware
- Ransom note (GIFtToDerek.txt)
- Encrypted headshot GIF (best.gif.Mugatu)
- Encrypted informant GIF (the_key_to_success_0000.gif.Mugatu)
Thanks,
Roy
:
- best.gif.Mugatu
- GIFtToDerek.txt
- Mugatuware.exe
- the_key_to_success_0000.gif.Mugatu
, , GIF -. , .Mugatu . Mugatuware.exe . , — . , , .
IDA , :
import ida_segment import ida_name import ida_bytes import ida_typeinf idata = ida_segment.get_segm_by_name('.idata') type_map = {} for addr in range(idata.start_ea, idata.end_ea, 4): name = ida_name.get_name(addr) if name: tp = ida_typeinf.idc_get_type(addr) if tp: type_map[name] = tp for addr in range(idata.start_ea, idata.end_ea, 4): imp = ida_bytes.get_dword(addr) if imp != 0: imp_name = ida_name.get_name(imp) name_part = imp_name.split('_')[-1] ida_name.set_name(addr, name_part + '_imp') if name_part in type_map: tp = type_map[name_part] ida_typeinf.apply_decl(addr, tp.replace('(', 'func(') + ';')
:
, , in-memory PE -. , CrazyPills!!! 。 , . Sleep , http -. , , , . , , , . .
- :
- ;
- ;
Mailslots ;really, really, really, ridiculously good looking gifs ;.gif . .Mugatu . GIFtToDerek.txt .
, — 8 . XOR CrazyPills!!! , . , :
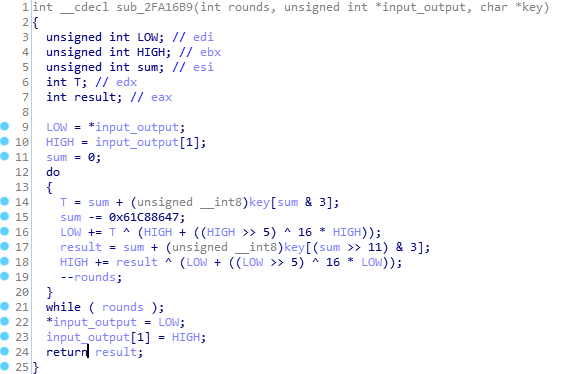
XTEA , — BYTE , DWORD . . Python :
def crypt(a, b, key): i = 0 for _ in range(32): t = (i + key[i & 3]) & 0xffffffff a = (a + (t ^ (b + ((b >> 5) ^ (b << 4))))) & 0xffffffff i = (0x100000000 + i - 0x61C88647) & 0xffffffff t = (i + key[(i >> 11) & 3]) & 0xffffffff b = (b + (t ^ (a + ((a >> 5) ^ (a << 4))))) & 0xffffffff return a, b def decrypt(a, b, key): i = 0xc6ef3720 for _ in range(32): t = (i + key[(i >> 11) & 3]) & 0xffffffff b = (0x100000000 + b - (t ^ (a + ((a >> 5) ^ (a << 4))))) & 0xffffffff i = (i + 0x61C88647) & 0xffffffff t = (i + key[i & 3]) & 0xffffffff a = (0x100000000 + a - (t ^ (b + ((b >> 5) ^ (b << 4))))) & 0xffffffff return a, b
, the_key_to_success_0000.gif.Mugatu . , . :

, , . C . GIF -.
#include <stdio.h> #include <unistd.h> void decrypt(unsigned int * inp, unsigned int * outp, unsigned char * key) { unsigned int i = 0xc6ef3720; unsigned int a = inp[0]; unsigned int b = inp[1]; unsigned int t; for(int j = 0; j < 32; j++) { t = i + key[(i >> 11) & 3]; b -= t ^ (a + ((a >> 5) ^ (a << 4))); i += 0x61C88647; t = i + key[i & 3]; a -= t ^ (b + ((b >> 5) ^ (b << 4))); } outp[0] = a; outp[1] = b; } int main() { int fd = open("best.gif.Mugatu", 0); unsigned int inp[2]; unsigned int outp[2]; unsigned int key = 0; read(fd, inp, 8); close(fd); for(unsigned long long key = 0; key < 0x100000000; key++) { if((key & 0xffffff) == 0) { printf("%lf\n", ((double)key) / ((double)0x100000000) * 100.0); } decrypt(inp, outp, &key); if( ((char *)outp)[0] == 'G' && ((char *)outp)[1] == 'I' && ((char *)outp)[2] == 'F' && ((char *)outp)[5] == 'a') { printf("%#llx\n", key); } } }
0xb1357331 :

0x0B — vv_max
Hey, at least its not subleq.
vv_max.exe , . 256- . AVX2 , vpermd , vpslld . - :
0000 clear_regs 0001 r0 = 393130324552414c46 0023 r1 = 3030303030303030303030303030303030303030303030303030303030303030 0045 r3 = 1a1b1b1b1a13111111111111111111151a1b1b1b1a1311111111111111111115 0067 r4 = 1010101010101010080408040201101010101010101010100804080402011010 0089 r5 = b9b9bfbf041310000000000000000000b9b9bfbf04131000 00ab r6 = 2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f2f 00cd r10 = 140014001400140014001400140014001400140014001400140014001400140 00ef r11 = 1100000011000000110000001100000011000000110000001100000011000 0111 r12 = ffffffff0c0d0e08090a040506000102ffffffff0c0d0e08090a040506000102 0133 r13 = ffffffffffffffff000000060000000500000004000000020000000100000000 0155 r16 = ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff 0177 r17 = 6a09e667bb67ae853c6ef372a54ff53a510e527f9b05688c1f83d9ab5be0cd19 0199 r18 = 428a2f9871374491b5c0fbcfe9b5dba53956c25b59f111f1923f82a4ab1c5ed5 01bb r19 = 300000002000000010000000000000007000000060000000500000004 01dd r20 = 0 01ff r21 = 100000001000000010000000100000001000000010000000100000001 0221 r22 = 200000002000000020000000200000002000000020000000200000002 0243 r23 = 300000003000000030000000300000003000000030000000300000003 0265 r24 = 400000004000000040000000400000004000000040000000400000004 0287 r25 = 500000005000000050000000500000005000000050000000500000005 02a9 r26 = 600000006000000060000000600000006000000060000000600000006 02cb r27 = 700000007000000070000000700000007000000070000000700000007 02ed r20 = vpermd(r0, r20) 02f1 r21 = vpermd(r0, r21) 02f5 r22 = vpermd(r0, r22) 02f9 r23 = vpermd(r0, r23) 02fd r24 = vpermd(r0, r24) 0301 r25 = vpermd(r0, r25) 0305 r26 = vpermd(r0, r26) 0309 r27 = vpermd(r0, r27) 030d r7 = vpsrld(r1, 4) 0311 r28 = r20 ^ r21 0315 r28 = r28 ^ r22 0319 r28 = r28 ^ r23 031d r28 = r28 ^ r24 0321 r28 = r28 ^ r25 0325 r28 = r28 ^ r26 0329 r28 = r28 ^ r27 032d r7 = r7 & r6 0331 r29 = vpslld(r17, 7) 0335 r30 = vpsrld(r17, 25) 0339 r15 = r29 | r30 033d r8 = vpcmpeqb(r1, r6) 0341 r29 = vpslld(r17, 21) 0345 r30 = vpsrld(r17, 11) 0349 r29 = r29 | r30 034d r15 = r15 ^ r29 0351 r8 = vpcmpeqb(r1, r6) 0355 r29 = vpslld(r17, 26) 0359 r30 = vpsrld(r17, 6) 035d r29 = r29 | r30 0361 r15 = r15 ^ r29 0365 r29 = r20 ^ r16 0369 r30 = r20 & r18 036d r29 = r29 ^ r30 0371 r15 = add_d(r29, r15) 0375 r20 = add_d(r15, r0) 0379 r7 = add_b(r8, r7) 037d r29 = r20 ^ r28 0381 r17 = vpermd(r29, r19) 0385 r7 = vpshufb(r5, r7) 0389 r29 = vpslld(r17, 7) 038d r30 = vpsrld(r17, 25) 0391 r15 = r29 | r30 0395 r29 = vpslld(r17, 21) 0399 r30 = vpsrld(r17, 11) 039d r29 = r29 | r30 03a1 r15 = r15 ^ r29 03a5 r29 = vpslld(r17, 26) 03a9 r30 = vpsrld(r17, 6) 03ad r29 = r29 | r30 03b1 r15 = r15 ^ r29 03b5 r2 = add_b(r1, r7) 03b9 r29 = r21 ^ r16 03bd r30 = r21 & r18 03c1 r29 = r29 ^ r30 03c5 r15 = add_d(r29, r15) 03c9 r21 = add_d(r15, r0) 03cd r29 = r21 ^ r28 03d1 r17 = vpermd(r29, r19) 03d5 r20 = r20 ^ r21 03d9 r29 = vpslld(r17, 7) 03dd r30 = vpsrld(r17, 25) 03e1 r15 = r29 | r30 03e5 r29 = vpslld(r17, 21) 03e9 r30 = vpsrld(r17, 11) 03ed r29 = r29 | r30 03f1 r15 = r15 ^ r29 03f5 r29 = vpslld(r17, 26) 03f9 r30 = vpsrld(r17, 6) 03fd r29 = r29 | r30 0401 r15 = r15 ^ r29 0405 r7 = vpmaddubsw(r2, r10) 0409 r29 = r22 ^ r16 040d r30 = r22 & r18 0411 r29 = r29 ^ r30 0415 r15 = add_d(r29, r15) 0419 r22 = add_d(r15, r0) 041d r29 = r22 ^ r28 0421 r17 = vpermd(r29, r19) 0425 r20 = r20 ^ r22 0429 r29 = vpslld(r17, 7) 042d r30 = vpsrld(r17, 25) 0431 r15 = r29 | r30 0435 r29 = vpslld(r17, 21) 0439 r30 = vpsrld(r17, 11) 043d r29 = r29 | r30 0441 r15 = r15 ^ r29 0445 r29 = vpslld(r17, 26) 0449 r30 = vpsrld(r17, 6) 044d r29 = r29 | r30 0451 r15 = r15 ^ r29 0455 r2 = vpmaddwd(r7, r11) 0459 r29 = r23 ^ r16 045d r30 = r23 & r18 0461 r29 = r29 ^ r30 0465 r15 = add_d(r29, r15) 0469 r23 = add_d(r15, r0) 046d r29 = r23 ^ r28 0471 r17 = vpermd(r29, r19) 0475 r20 = r20 ^ r23 0479 r29 = vpslld(r17, 7) 047d r30 = vpsrld(r17, 25) 0481 r15 = r29 | r30 0485 r29 = vpslld(r17, 21) 0489 r30 = vpsrld(r17, 11) 048d r29 = r29 | r30 0491 r15 = r15 ^ r29 0495 r29 = vpslld(r17, 26) 0499 r30 = vpsrld(r17, 6) 049d r29 = r29 | r30 04a1 r15 = r15 ^ r29 04a5 r29 = r24 ^ r16 04a9 r30 = r24 & r18 04ad r29 = r29 ^ r30 04b1 r15 = add_d(r29, r15) 04b5 r24 = add_d(r15, r0) 04b9 r29 = r24 ^ r28 04bd r17 = vpermd(r29, r19) 04c1 r20 = r20 ^ r24 04c5 r29 = vpslld(r17, 7) 04c9 r30 = vpsrld(r17, 25) 04cd r15 = r29 | r30 04d1 r29 = vpslld(r17, 21) 04d5 r30 = vpsrld(r17, 11) 04d9 r29 = r29 | r30 04dd r15 = r15 ^ r29 04e1 r29 = vpslld(r17, 26) 04e5 r30 = vpsrld(r17, 6) 04e9 r29 = r29 | r30 04ed r15 = r15 ^ r29 04f1 r29 = r25 ^ r16 04f5 r30 = r25 & r18 04f9 r29 = r29 ^ r30 04fd r15 = add_d(r29, r15) 0501 r25 = add_d(r15, r0) 0505 r29 = r25 ^ r28 0509 r17 = vpermd(r29, r19) 050d r20 = r20 ^ r25 0511 r2 = vpshufb(r2, r12) 0515 r29 = vpslld(r17, 7) 0519 r30 = vpsrld(r17, 25) 051d r15 = r29 | r30 0521 r29 = vpslld(r17, 21) 0525 r30 = vpsrld(r17, 11) 0529 r29 = r29 | r30 052d r15 = r15 ^ r29 0531 r29 = vpslld(r17, 26) 0535 r30 = vpsrld(r17, 6) 0539 r29 = r29 | r30 053d r15 = r15 ^ r29 0541 r29 = r26 ^ r16 0545 r30 = r26 & r18 0549 r29 = r29 ^ r30 054d r15 = add_d(r29, r15) 0551 r26 = add_d(r15, r0) 0555 r29 = r26 ^ r28 0559 r17 = vpermd(r29, r19) 055d r20 = r20 ^ r26 0561 r29 = vpslld(r17, 7) 0565 r30 = vpsrld(r17, 25) 0569 r15 = r29 | r30 056d r29 = vpslld(r17, 21) 0571 r30 = vpsrld(r17, 11) 0575 r29 = r29 | r30 0579 r15 = r15 ^ r29 057d r29 = vpslld(r17, 26) 0581 r30 = vpsrld(r17, 6) 0585 r29 = r29 | r30 0589 r15 = r15 ^ r29 058d r2 = vpermd(r2, r13) 0591 r29 = r27 ^ r16 0595 r30 = r27 & r18 0599 r29 = r29 ^ r30 059d r15 = add_d(r29, r15) 05a1 r27 = add_d(r15, r0) 05a5 r29 = r27 ^ r28 05a9 r17 = vpermd(r29, r19) 05ad r20 = r20 ^ r27 05b1 r19 = ffffffffffffffffffffffffffffffffffffffffffffffff 05d3 r20 = r20 & r19 05d7 r31 = 2176620c3a5c0f290b583618734f07102e332623780e59150c05172d4b1b1e22
FLARE2019 . , , . , FLARE2019 . r2 r20 . , r20 . r2 — 6 r2 . , 6 . Frida :
// vvmax.js var modules = Process.enumerateModules(); var base = modules[0].base; Interceptor.attach(base.add(0x1665), function() { var p = this.context.rdx.add(0x840); var res = p.readByteArray(32); send(null, res); });
:
0x0C — help
You're my only hope FLARE-On player! One of our developers was hacked and we're not sure what they took. We managed to set up a packet capture on the network once we found out but they were definitely already on the system. I think whatever they installed must be buggy — it looks like they crashed our developer box. We saved off the dump file but I can't make heads or tails of it — PLEASE HELP!!!!!!
. RAM - . 4444 , 6666 , 7777 8888 . , , , RAM -. volatility . volatility Win10x64_15063 , , Win7SP1x64 , .
volatility :
$ volatility --profile Win7SP1x64 -f help.dmp modules Volatility Foundation Volatility Framework 2.6 Offset(V) Name Base Size File ------------------ -------------------- ------------------ ------------------ ---- 0xfffffa800183e890 ntoskrnl.exe 0xfffff80002a49000 0x5e7000 \SystemRoot\system32\ntoskrnl.exe ... 0xfffffa800428ff30 man.sys 0xfffff880033bc000 0xf000 \??\C:\Users\FLARE ON 2019\Desktop\man.sys
:
$ volatility --profile Win7SP1x64 -f help.dmp moddump --base 0xfffff880033bc000 -D drivers Volatility Foundation Volatility Framework 2.6 Module Base Module Name Result ------------------ -------------------- ------ 0xfffff880033bc000 man.sys Error: e_magic 0000 is not a valid DOS signature.
, . volshell .
$ volatility --profile Win7SP1x64 -f help.dmp volshell In [1]: db(0xfffff880033bc000) 0xfffff880033bc000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc040 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc050 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc060 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xfffff880033bc070 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ In [2]: db(0xfffff880033bc000 + 0x1100) 0xfffff880033bd100 01 48 8b 4c 24 20 48 8b 44 24 28 48 89 41 08 48 .HL$.HD$(HAH 0xfffff880033bd110 83 c4 18 c3 cc cc cc cc cc cc cc cc cc cc cc cc ................ 0xfffff880033bd120 48 89 4c 24 08 48 83 ec 38 48 8b 44 24 40 0f be HL$.H..8H.D$@.. 0xfffff880033bd130 48 43 48 8b 44 24 40 0f be 40 42 83 c0 01 3b c8 HCH.D$@..@B...;. 0xfffff880033bd140 7e 27 45 33 c9 41 b8 15 5b 00 00 48 8d 15 de 44 ~'E3.A..[..H...D 0xfffff880033bd150 00 00 48 8d 0d 07 45 00 00 ff 15 71 4f 00 00 c7 ..H...E....qO... 0xfffff880033bd160 44 24 20 00 00 00 00 eb 08 c7 44 24 20 01 00 00 D$........D$.... 0xfffff880033bd170 00 48 8b 44 24 40 48 8b 80 b8 00 00 00 48 83 c4 .HD$@H......H.. In [4]: man = addrspace().read(0xfffff880033bc000, 0xf000) In [5]: with open('man_writeup.sys', 'wb') as f: ...: f.write(man) ...:
, , moddump . . . - , , .
RC4 . , .
user-space . DLL - . DLL - ( m.dll ), . , . :
- (
+0x8 ) _EPROCESS ( +0x68 )- (
+0x48 ) - (
+0x58 )
DLL - RC4 , 0x2c - , 0x48 .
volatility volshell :
import struct from Crypto.Cipher import ARC4 head = 0xfffff880033c8158 krnl = addrspace() def u64(x): return struct.unpack('Q', x)[0] fd = u64(krnl.read(head, 8)) while True: proc_addr = u64(krnl.read(fd + 0x68, 8)) base = u64(krnl.read(fd + 0x48, 8)) key = krnl.read(fd + 0x48, 0x2c) sz = u64(krnl.read(fd + 0x58, 8)) fd = u64(krnl.read(fd, 8)) p = obj.Object('_EPROCESS', proc_addr, krnl) print p.ImageFileName.v(), hex(proc_addr), hex(base), hex(sz) proc_space = p.get_process_address_space() dump = proc_space.read(base, sz) if dump[:0x100] == '\x00' * 0x100: dump = ARC4.new(key).decrypt(dump) with open('proc_{:016x}'.format(base), 'wb') as f: f.write(dump) if fd == head: break
, , RC4 . IDA , , :
IDA from __future__ import print_function import sys import re from idaapi import get_func, decompile, get_name_ea, auto_wait, BADADDR from idaapi import cot_call, cot_obj, init_hexrays_plugin, qexit import ida_typeinf import ida_lines def rc4(key, data): S = list(range(256)) j = 0 for i in list(range(256)): j = (j + S[i] + ord(key[i % len(key)])) % 256 S[i], S[j] = S[j], S[i] j = 0 y = 0 out = [] for char in data: j = (j + 1) % 256 y = (y + S[j]) % 256 S[j], S[y] = S[y], S[j] out.append(chr(ord(char) ^ S[(S[j] + S[y]) % 256])) return ''.join(out) def decrypt_stack_str_args(ea): func = get_func(ea) if func is None: return try: c_func = decompile(func) c_func.pseudocode except Exception as ex: return for citem in c_func.treeitems: citem = citem.to_specific_type if citem.is_expr() and\ citem.op == cot_call and\ citem.ea == ea: args = [] key = citem.a[0] key_len = citem.a[1] s = citem.a[2] s_len = citem.a[3] def get_var_idx(obj): while obj.opname != 'var': if obj.opname in ('ref', 'cast'): obj = obj.x else: raise Exception('can\'t find type') return obj.v.idx if key_len.opname != 'num' or s_len.opname != 'num': print('[!] can\'t get length: 0x{:08x}'.format(ea)) else: try: key_len_val = key_len.n._value s_len_val = s_len.n._value print('0x{:08x}'.format(ea), 'key_len =', key_len_val, ', s_len =', s_len_val) hx_view = idaapi.open_pseudocode(ea, -1) key_var_stkoff = hx_view.cfunc.get_lvars()[get_var_idx(key)].location.stkoff() s_var_stkoff = hx_view.cfunc.get_lvars()[get_var_idx(s)].location.stkoff() key_var = [v for v in hx_view.cfunc.get_lvars() if v.location.stkoff() == key_var_stkoff][0] tif = ida_typeinf.tinfo_t() ida_typeinf.parse_decl(tif, None, 'unsigned __int8 [{}];'.format(key_len_val), 0) hx_view.set_lvar_type(key_var, tif) s_var = [v for v in hx_view.cfunc.get_lvars() if v.location.stkoff() == s_var_stkoff][0] tif = ida_typeinf.tinfo_t() ida_typeinf.parse_decl(tif, None, 'unsigned __int8 [{}];'.format(s_len_val + 1), 0) hx_view.set_lvar_type(s_var, tif) key_var = [v for v in hx_view.cfunc.get_lvars() if v.location.stkoff() == key_var_stkoff][0] s_var = [v for v in hx_view.cfunc.get_lvars() if v.location.stkoff() == s_var_stkoff][0] key_regex = re.compile('{}\[(.+)\] = (.+);'.format(key_var.name)) s_regex = re.compile('{}\[(.+)\] = (.+);'.format(s_var.name)) key = bytearray(key_len_val) s = bytearray(s_len_val + 1) src = '\n'.join([ida_lines.tag_remove(i.line) for i in hx_view.cfunc.pseudocode]) for i, j in s_regex.findall(src): s[int(i)] = (0x100 + int(j)) & 0xff for i, j in key_regex.findall(src): key[int(i)] = (0x100 + int(j)) & 0xff key = ''.join(chr(i) for i in key) s = ''.join(chr(i) for i in s) result = rc4(key, s[:-1])
:

. :
m.dll — , . 4444 . — ;n.dll — 192.168.1.243 ;c.dll — RC4 . ;k.dll — (keylogger);s.dll — ;f.dll — .
, XOR 8. 4444 , .. . : , — . , - .
( 4444 ) . , - . , . :
- keys.kdb
- C:\
- C:\keypass\keys.kdb
, f.dll : keys.kdb , .
6666 . LZNT1 RC4 XOR . , XOR - , .. . RC4 , RAM -: FLARE ON 2019 . , GetUserNameA , , - , RC4 . LZNT1 :
from ctypes import * nt = windll.ntdll for fname in ['input']: with open(fname, 'rb') as f: buf = f.read() dec_data = create_string_buffer(0x10000) final_size = c_ulong(0) status = nt.RtlDecompressBuffer( 0x102,
6666 . :
00000000: CC 69 94 FA 6A 37 18 29 CB 8D 87 EF 11 63 8E 73 .i..j7.).....cs 00000010: FE AB 43 3B B3 94 28 4B 4D 19 00 00 00 4F DB C7 ..C;..(KM....O.. 00000020: F3 1E E4 13 15 34 8F 51 A9 2B C2 D7 C1 96 78 F7 .....4.Q.+....x. 00000030: 91 98
, :
00000000: 19 00 00 00 4F DB C7 F3 1E E4 13 15 34 8F 51 A9 ....O.......4.Q. 00000010: 2B C2 D7 C1 96 78 F7 91 98 +....x...
4 — , 25. :
00000000: 12 B0 00 43 3A 5C 6B 65 79 70 61 04 73 73 01 70 ...C:\keypa.ss.p 00000010: 73 2E 6B 64 62 s.kdb
C:\keypass\keys.kdb . , , . 6666 — KeePass .
7777 BMP . XOR , , , .. . , , KeePass .


8888 k.dll — .
C:\Windows\system32\cmd.exe nslookup googlecom ping 1722173110 nslookup soeblogcom nslookup fiosquatumgatefiosrouterhome C:\Windows\system32\cmd.exe Start Start menu Start menu chrome www.flare-on.com - Google Chrome tis encrypting something twice better than once Is encrypting something twice better than once? - Google Search - Google Chrome Start Start menu Start menu keeKeePass <DYN_TITLE> th1sisth33nd111 KeePass keys.kdb - KeePass Is encrypting something twice better than once? - Google Search - Google Chrome Start Start menu Start menu KeePass <DYN_TITLE> th1sisth33nd111 Open Database - keys.kdb KeePass Start Start menu Start menu KeePass Start menu Start menu Start menu KeePass <DYN_TITLE> th1sisth33nd111
th1sisth33nd111 , . , . , keylogger . , , ping . hashcat KeePass , . :
$ strings help.dmp | grep -i '3nd!' !s_iS_th3_3Nd!!!
Th .
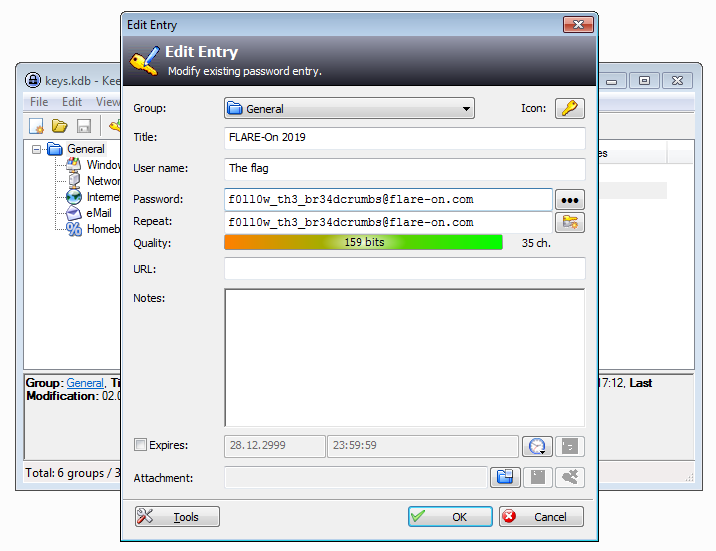
. , -.
0x0D —
, . , , . , volatility , . ( UTC+3:00):